Last post was about “How To Implement Hytrust KMS for vSAN & VM Encryption?” which covered implementation of Hytrust and configuration with vCenter.
Scope of this post is to demonstrate on how to configure vSAN encryption and VM encryption!
vSAN encryption: Now, we are all set to enable vSAN encryption and this activity can take quite some time based on the size of vSAN datastore and many other factors.
Step 1: Login to vCSA, navigate to cluster Configure tab and under services, edit Encryption services.
Step 2:From the drop down list of KMS cluster, select the appropriate KMS cluster. In my case, its called “kms-Hytrust” and click “Apply”
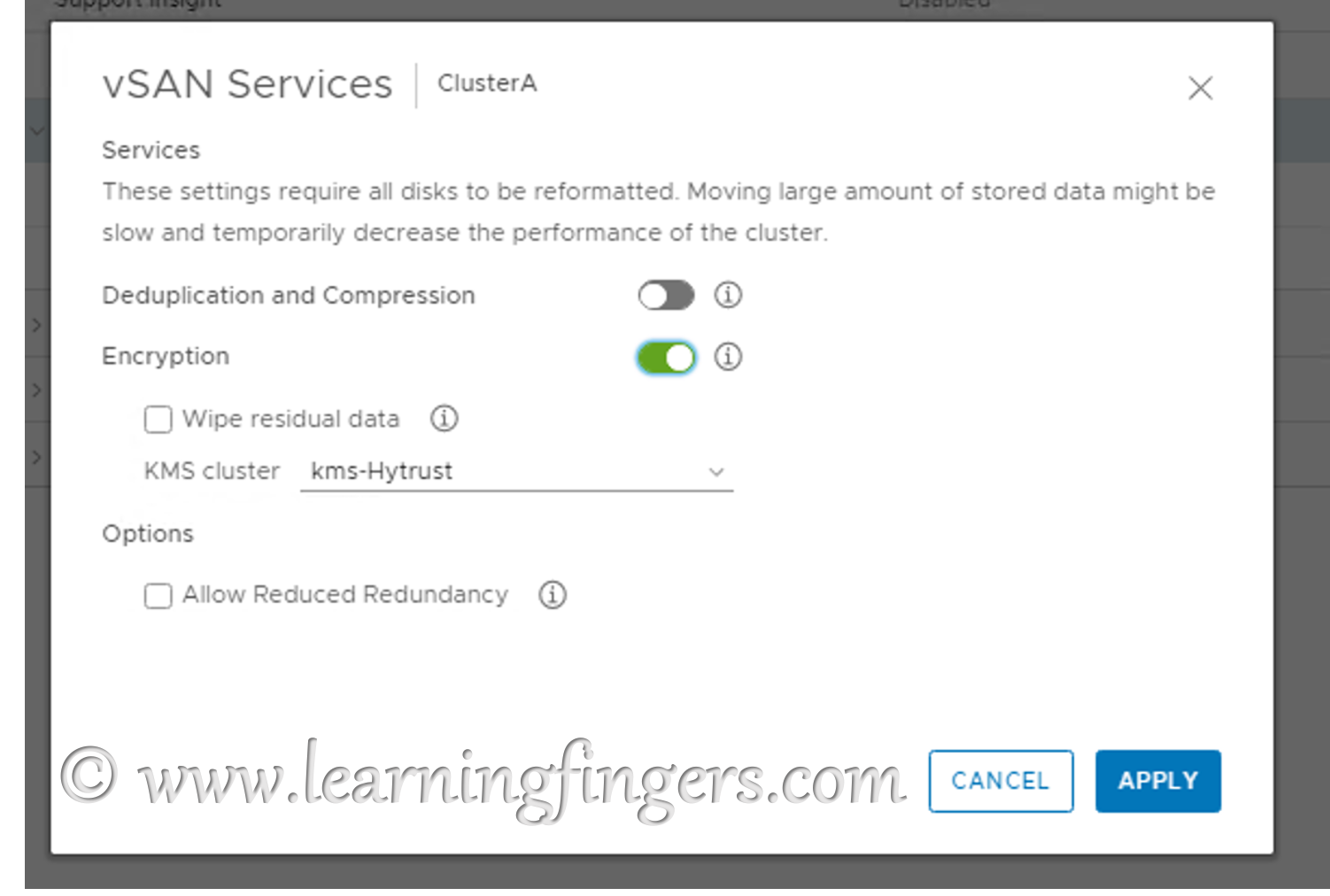
- Wipe residual data (formerly Erase disks before use) – Useful for disks that already have data on them. This wipes any data from the disk before encryption occurs.
- Allow Reduced Redundancy – vSAN will reduce the protection level during the enable/disable process. This is typically used only when a vSAN cluster is at the maximum number of hosts or fault domains required to meet a protection policy.
As for me both condition are not applicable, i used them in default mode.
Recommendations for “Wipe residual data” when using vSAN Encryption are:
- Select “Wipe residual data”
- When enabling vSAN Encryption for existing vSAN clusters that have vSAN objects on them
- When adding a host that has data on local devices to an encrypted vSAN cluster
- When performing a rekey operation to invoke a deep rekey (requesting a new KEK and new unique DEKs created for each vSAN storage device)
- Deselect “Wipe residual data”
- When enabling vSAN Encryption for a new vSAN cluster that has not previously had data on the vSAN devices
- When adding a host that has not had data on local devices that is being added to an encrypted vSAN cluster
- When performing a rekey operation to invoke a shallow rekey (only requesting a new KEK)
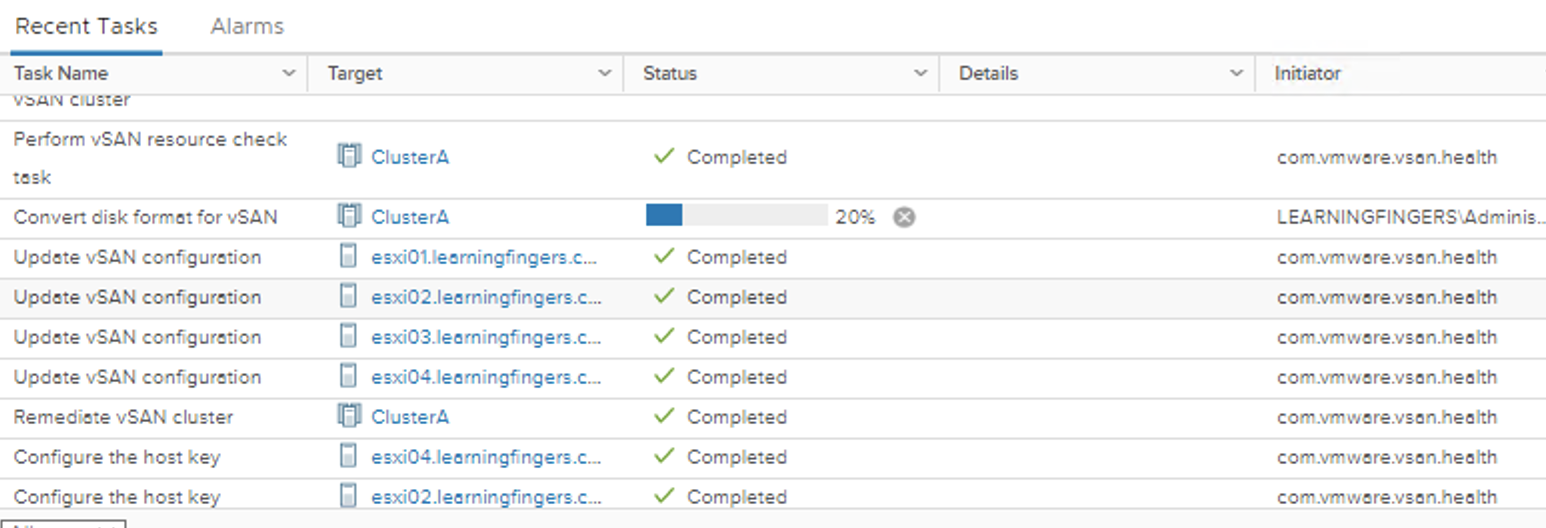
Output: 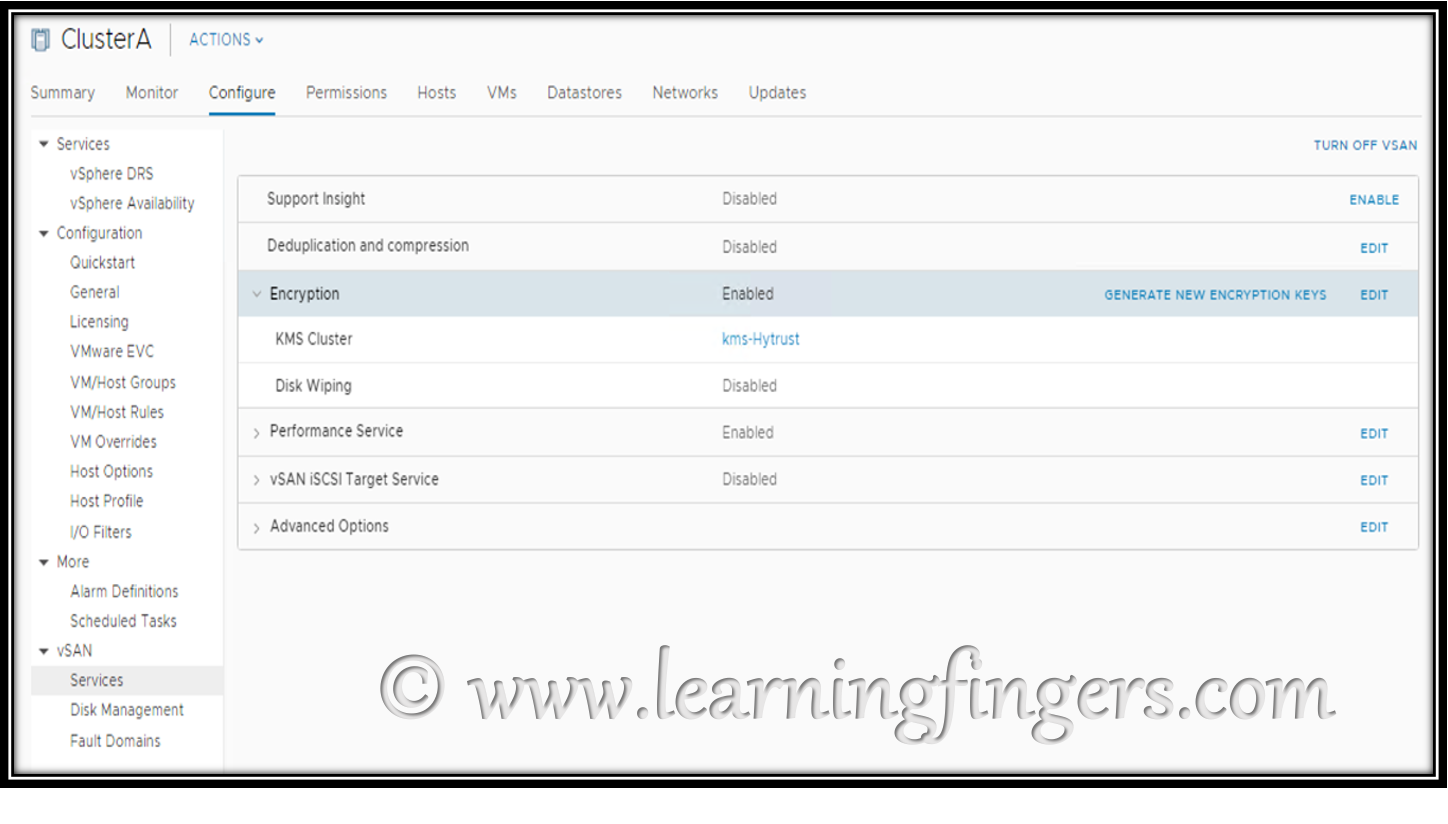
VM encryption:
Data encryption keys (DEKs) is generated by ESXi host based on Key encryption key (KEK) requested from KMS server through vCenter and is used to encrypt Virtual Machine files like NVRAM, VSWP, and VMSN files.The key that vCenter Server retrieves from the KMS unlocks an encrypted bundle in the VMX file that contains internal keys and other secrets.
Its very important to know, what is not encrypted:
– VMDK descriptor
– logs files
– some parts of configuration files like VMX & VMSD files
Lets jump into how to enable?
Case 1: We will use the default VM encryption policy called “VM Encryption Policy” to enable encryption on an existing VM!
Navigate to Virtual machine’s edit setting -> VM Options -> Encryption and switch the policy to “VM Encryption Policy“ 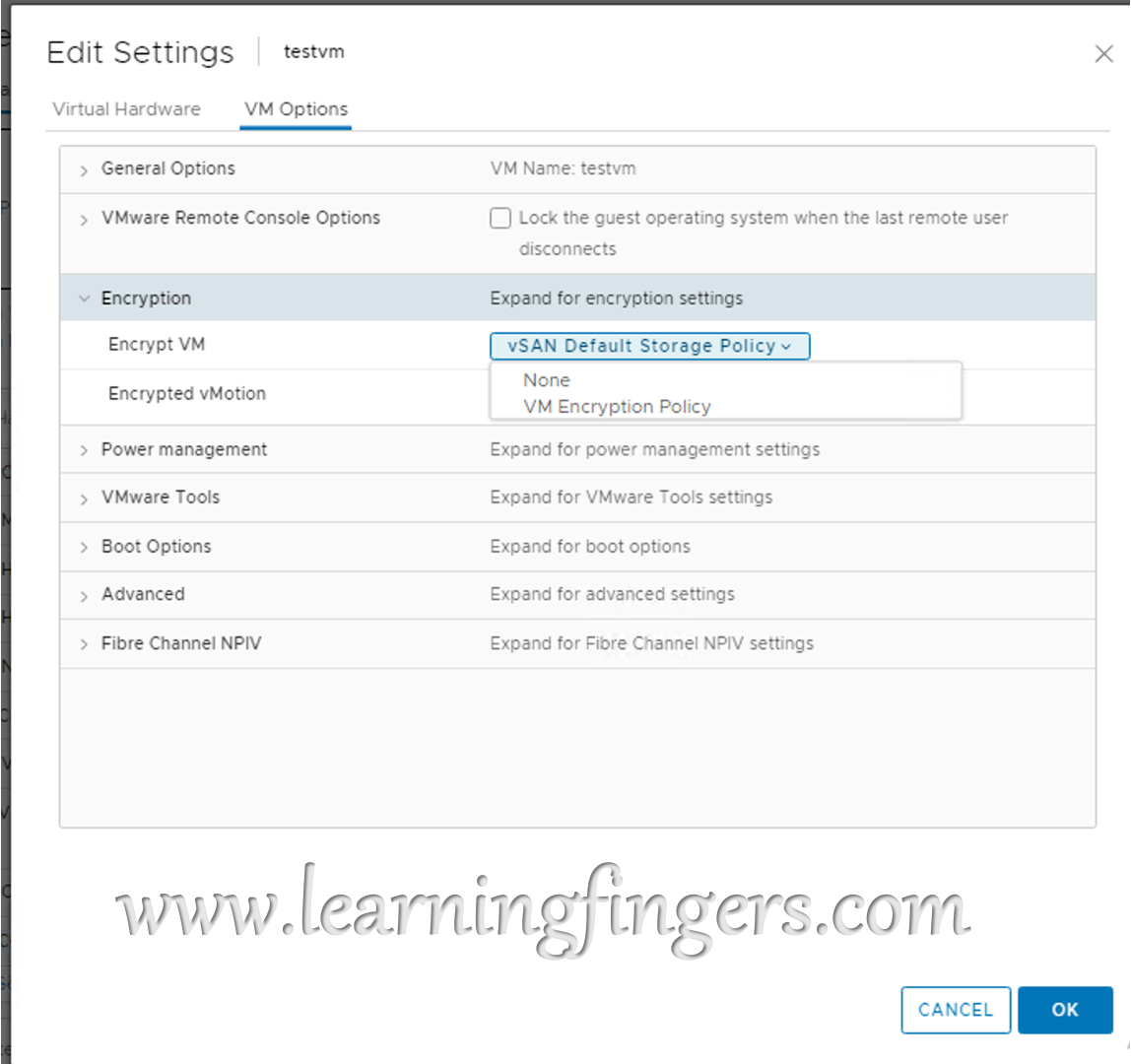
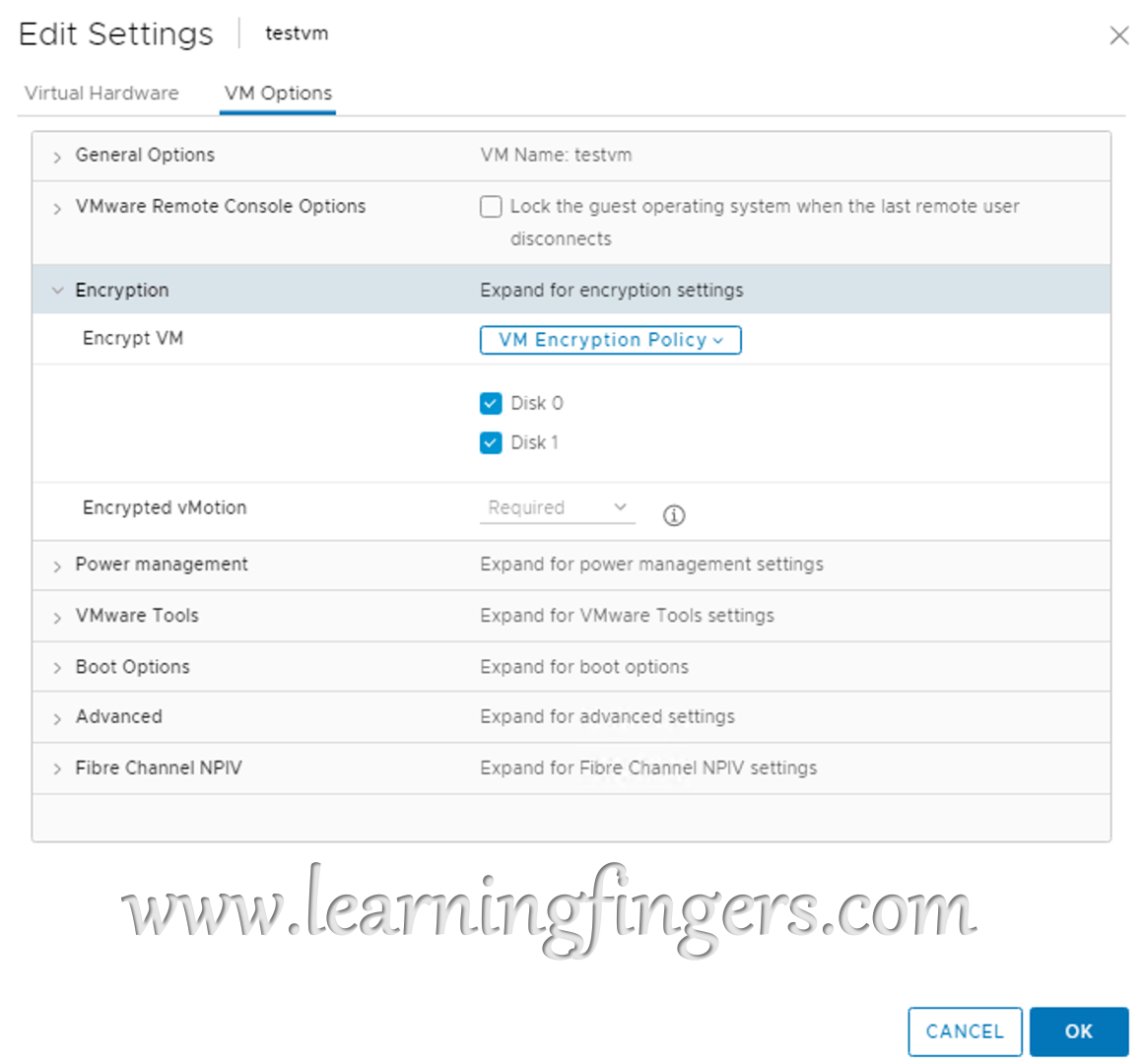
Check box gives you the possibility of encrypt all the disk attached to the virtual machine or selected. As soon as the task is completed, we see the confirmation on the summary page of the VM.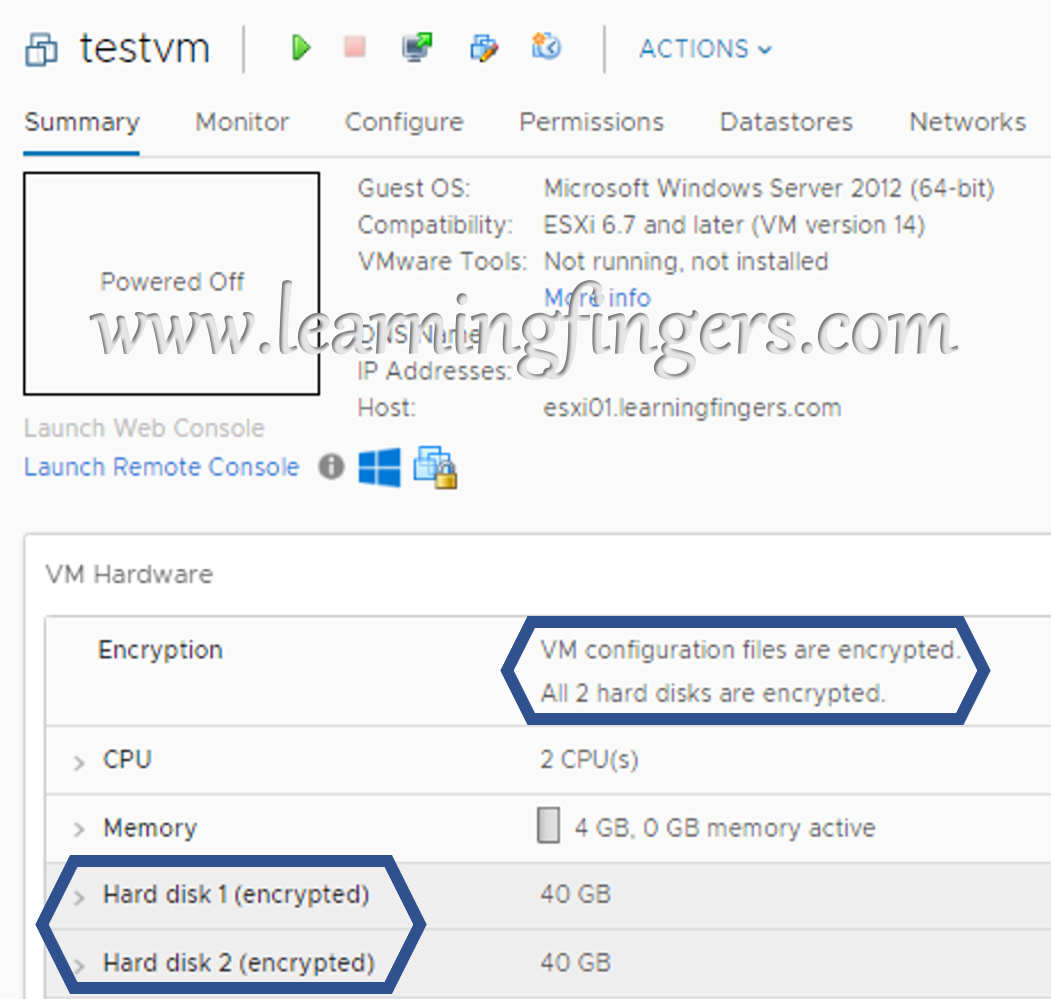
Case 2: We will use the default VM encryption policy called “VM Encryption Policy” to enable encryption on an new VM! While creating new VM change the policy and that’s it.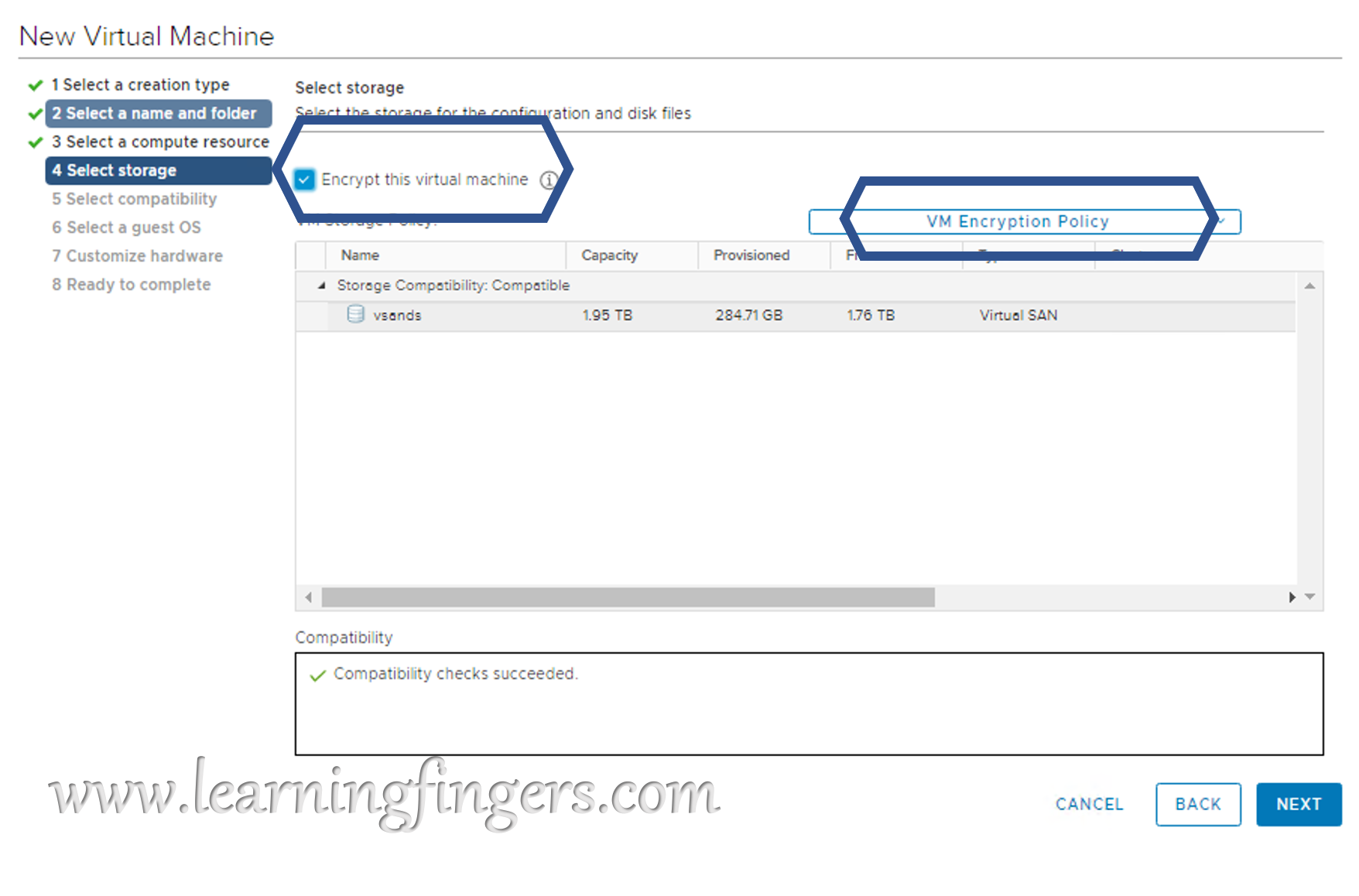

Hope this helps you!
- How to Implement Hytrust KMS and enable vSAN encryption? - 16/10/2022
- How to delete Inaccessible objects in vSAN datastore? - 16/09/2022
- Availability options with vROPs 8. - 04/07/2022