Agenda of this post is to share my 2-cents on certificate integration with Cloud director 10.1.
If your question is, why VMware Cloud Director requires certificate then answer is “Secure communication between clients and servers and per cell it require two SSL certificates”.
These two certificates are used for two different SSL endpoint:
– For HTTPS communication
– For console proxy communication
Product allows us to use either wildcard or name sake certificates and VMware documents also reflect about 2 ways of integration:
- If you already have your own private key and CA-signed certificate files.
- If you want to use, system generated key – default (2048-bit) or Custom (As per requirement but no less than 1024 bits) and CA-signed certificate files.
For the sake of this post, i am using Windows based Certificate Authority and System generated SSL certificate. Without taking any longer, let’s jump in.
Step 1: Take a SSH session of vCD cell and make a copy of certificates.ks file.
Certificates.ks file has information of all SSL certificates generated and their private keys. 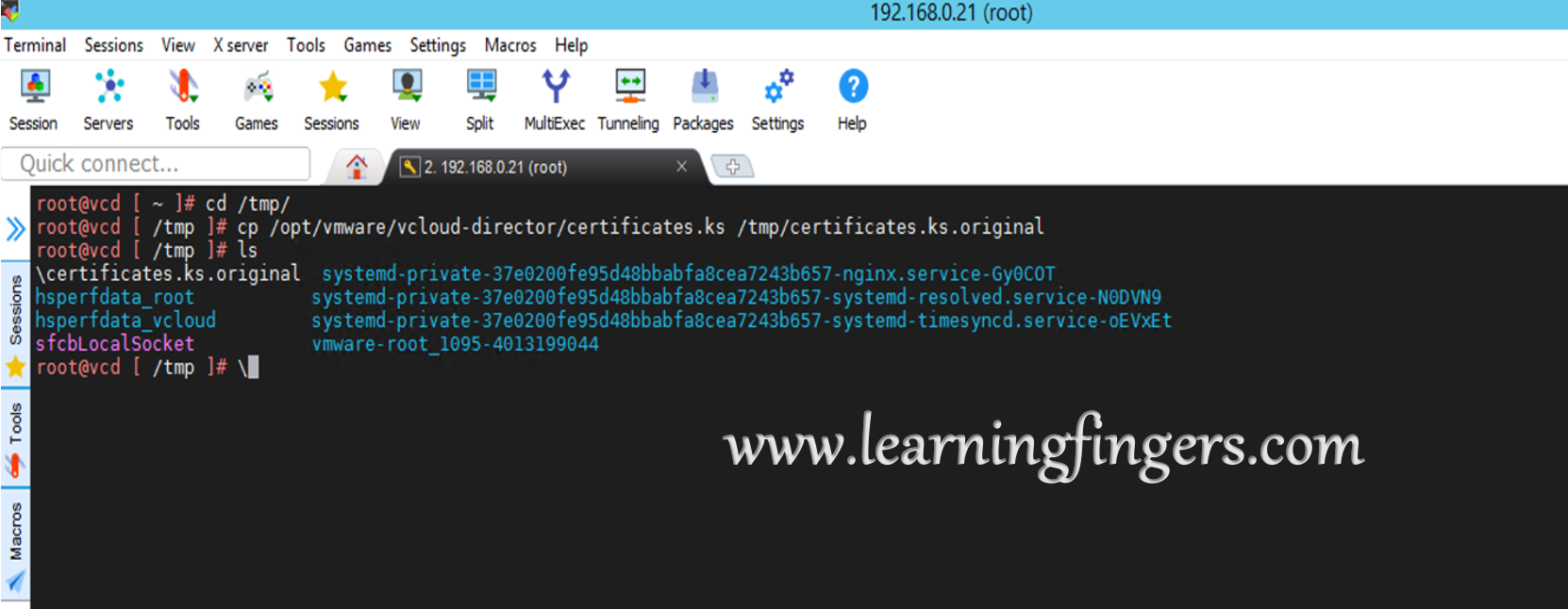
Step 2: Now we are going to create a set of private and public keys with required size. I am using default values of “2048-bit key length and expires one year after creation” which can be modified by adding “-keysize 4096 -validity 3650” where password used is root123 .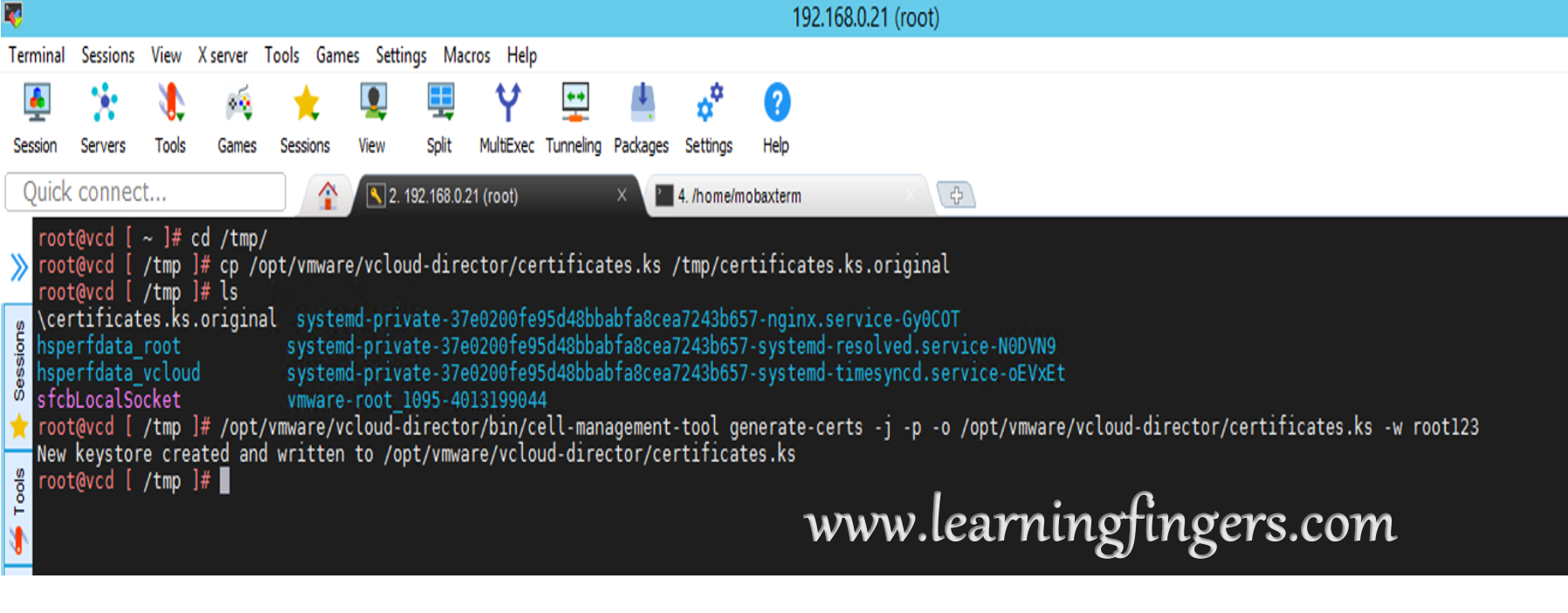
/opt/vmware/vcloud-director/bin/cell-management-tool generate-certs -j -p -o /opt/vmware/vcloud-director/certificates.ks -w root123
Step 3: After keys, its turn of CSR files. We are going to generate CSR files for HTTPS service and Console Proxy service.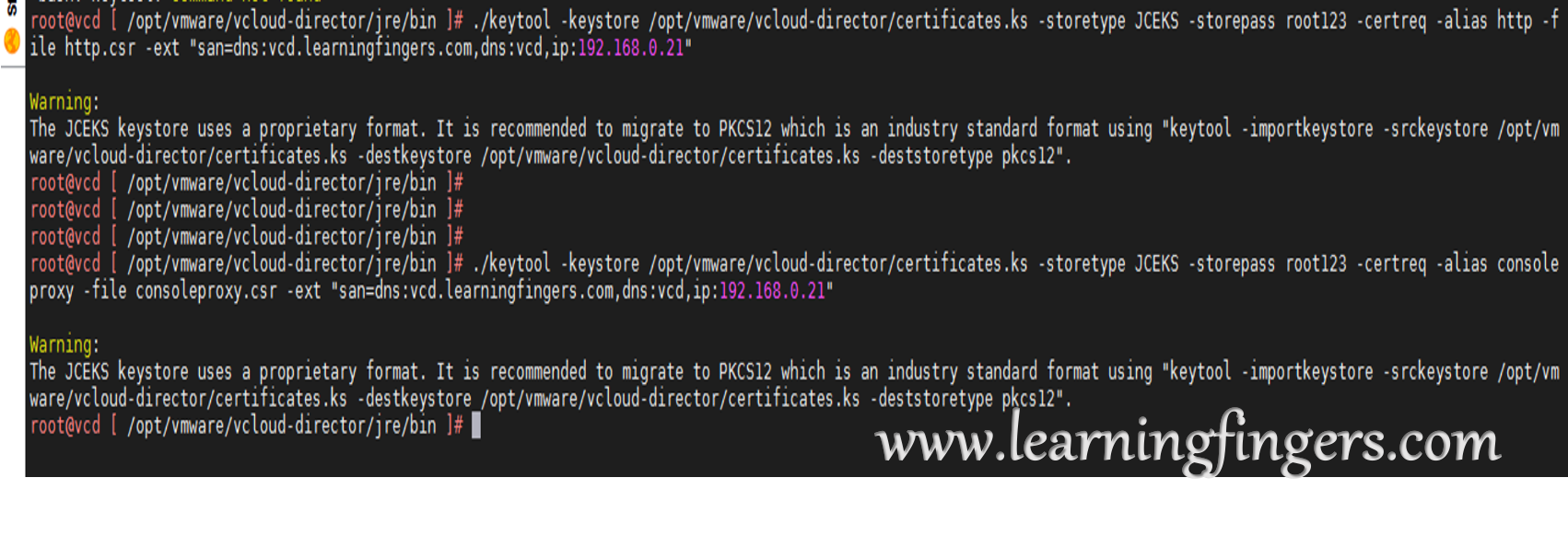
./keytool -keystore /opt/vmware/vcloud-director/certificates.ks -storetype JCEKS -storepass root123 -certreq -alias http -file http.csr -ext "san=dns:vcd.learningfingers.com,dns:vcd,ip:192.168.0.21" ./keytool -keystore /opt/vmware/vcloud-director/certificates.ks -storetype JCEKS -storepass root123 -certreq -alias consoleproxy -file consoleproxy.csr -ext "san=dns:vcd.learningfingers.com,dns:vcd,ip:192.168.0.21"
Step 4: These CSR files needs to be moved to CA server to get signed and imported back as certificates and in total we will have 3 certificates:
– CA root certificate
– HTTPS certificate
– Console Proxy certificate
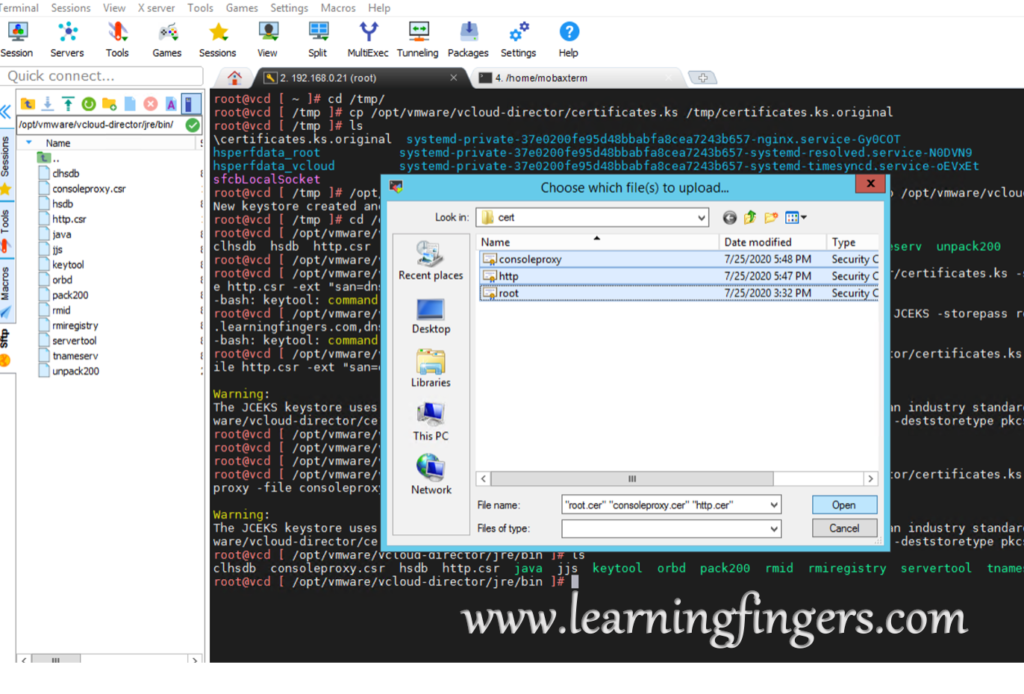
Step 5: Import all 3 signed certificates into the JCEKS keystore.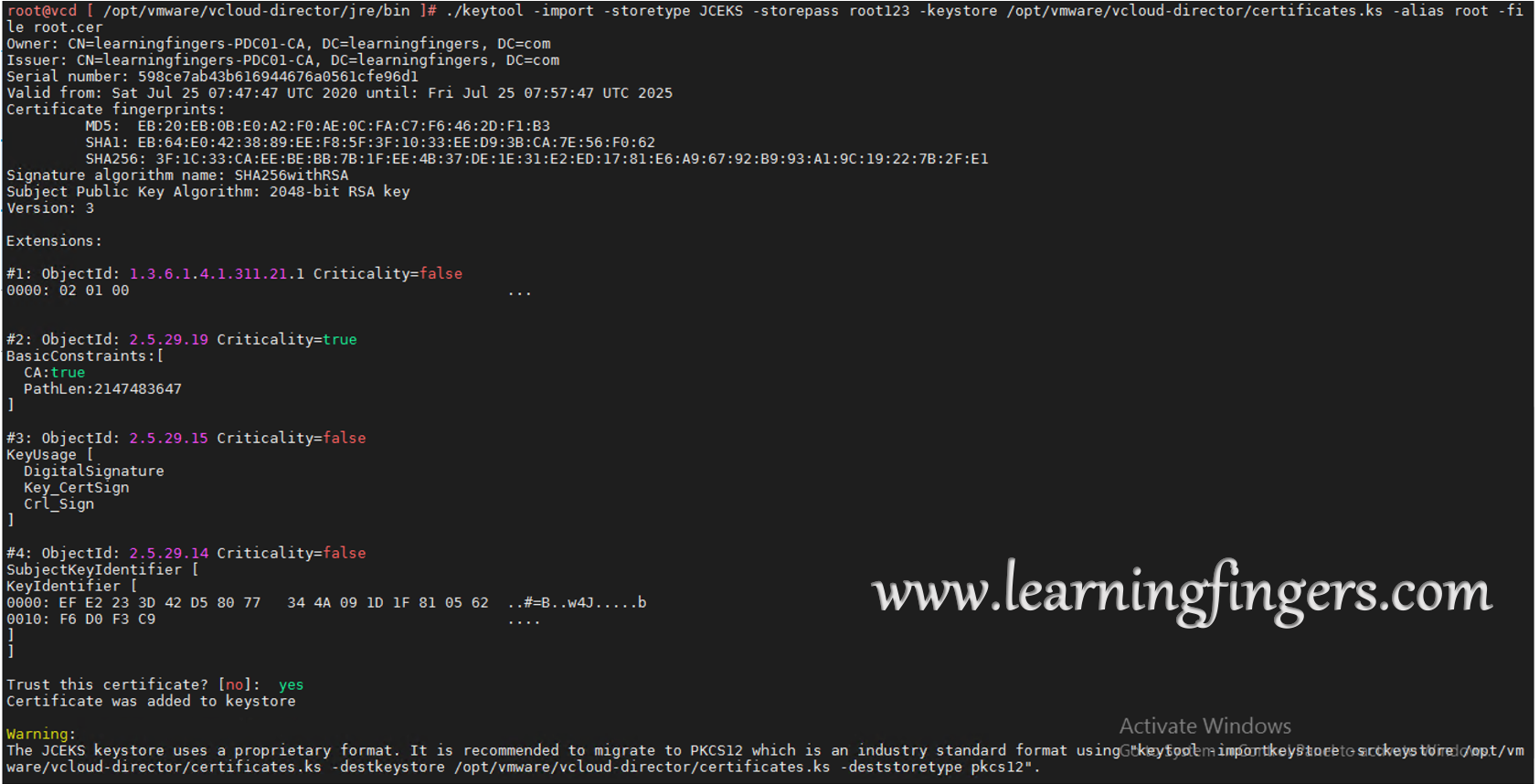
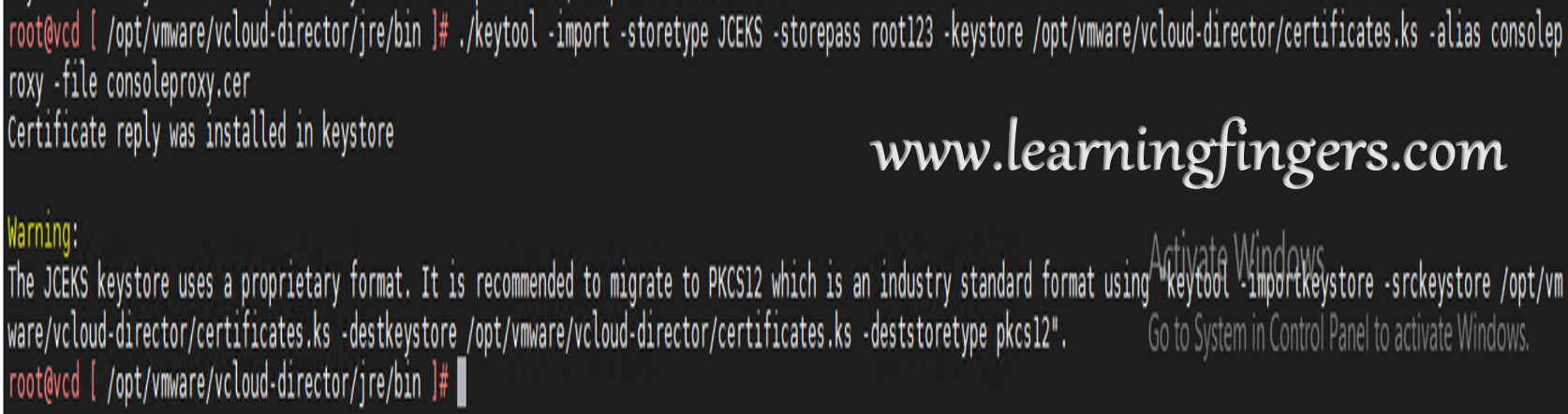
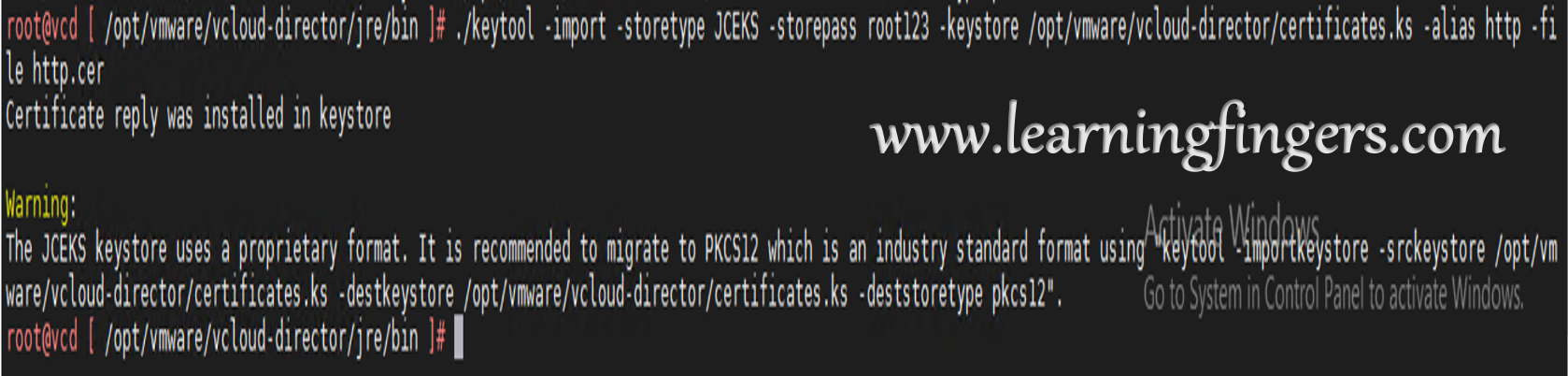
./keytool -import -storetype JCEKS -storepass root123 -keystore /opt/vmware/vcloud-director/certificates.ks -alias root -file root.cer ./keytool -import -storetype JCEKS -storepass root123 -keystore /opt/vmware/vcloud-director/certificates.ks -alias http -file http.cer ./keytool -import -storetype JCEKS -storepass root123 -keystore /opt/vmware/vcloud-director/certificates.ks -alias consoleproxy -file consoleproxy.cer
Confirmation for Step 5:
We need to ensure that all 3 certificates are successfully added in the keystore file.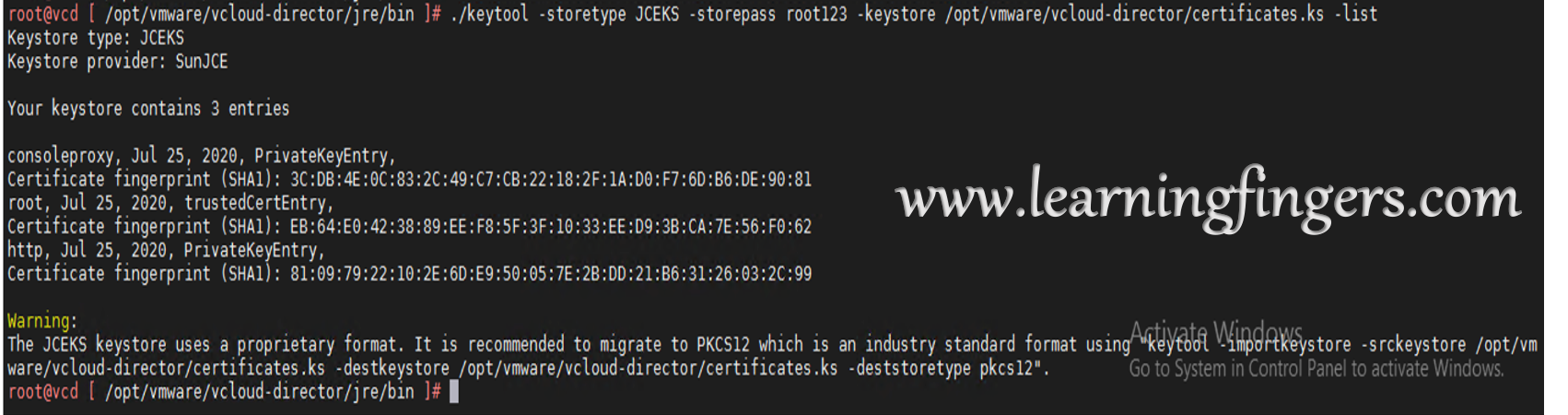
./keytool -storetype JCEKS -storepass root123 -keystore /opt/vmware/vcloud-director/certificates.ks -list
Step 6: Import the certificates into the VMware Cloud Director instance.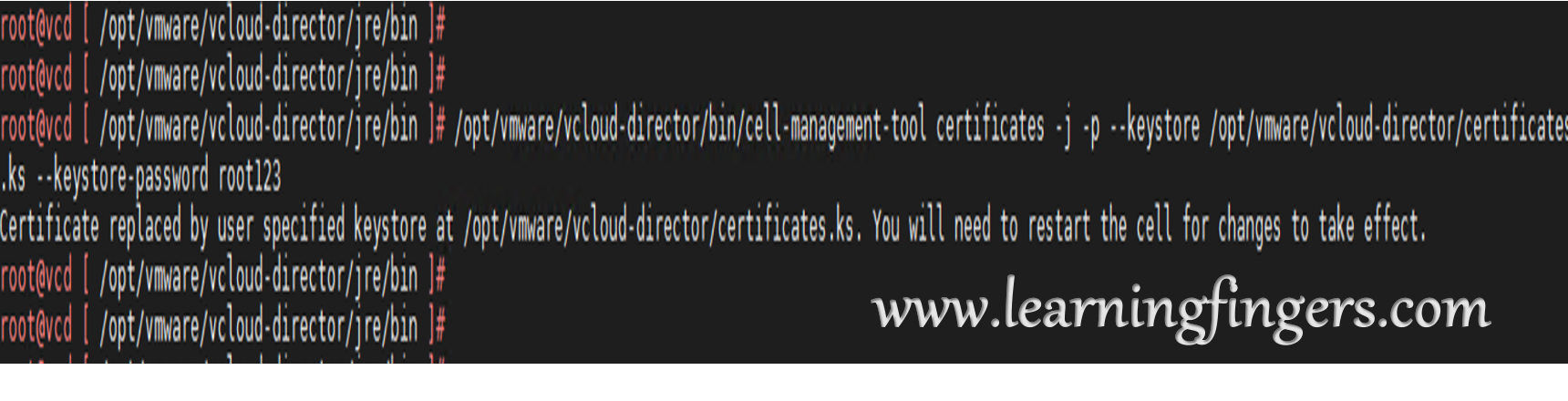
/opt/vmware/vcloud-director/bin/cell-management-tool certificates -j -p --keystore /opt/vmware/vcloud-director/certificates.ks --keystore-password root123
Step 7: As shown in step 6, we need to restart the cell for changes to take effect.
Service vmware-vcd restart
Give it couple of minutes to restart and then we can move towards final confirmation for certificate modification.
Confirmation:
Simplest way to confirm is from VMware Cloud Director login page.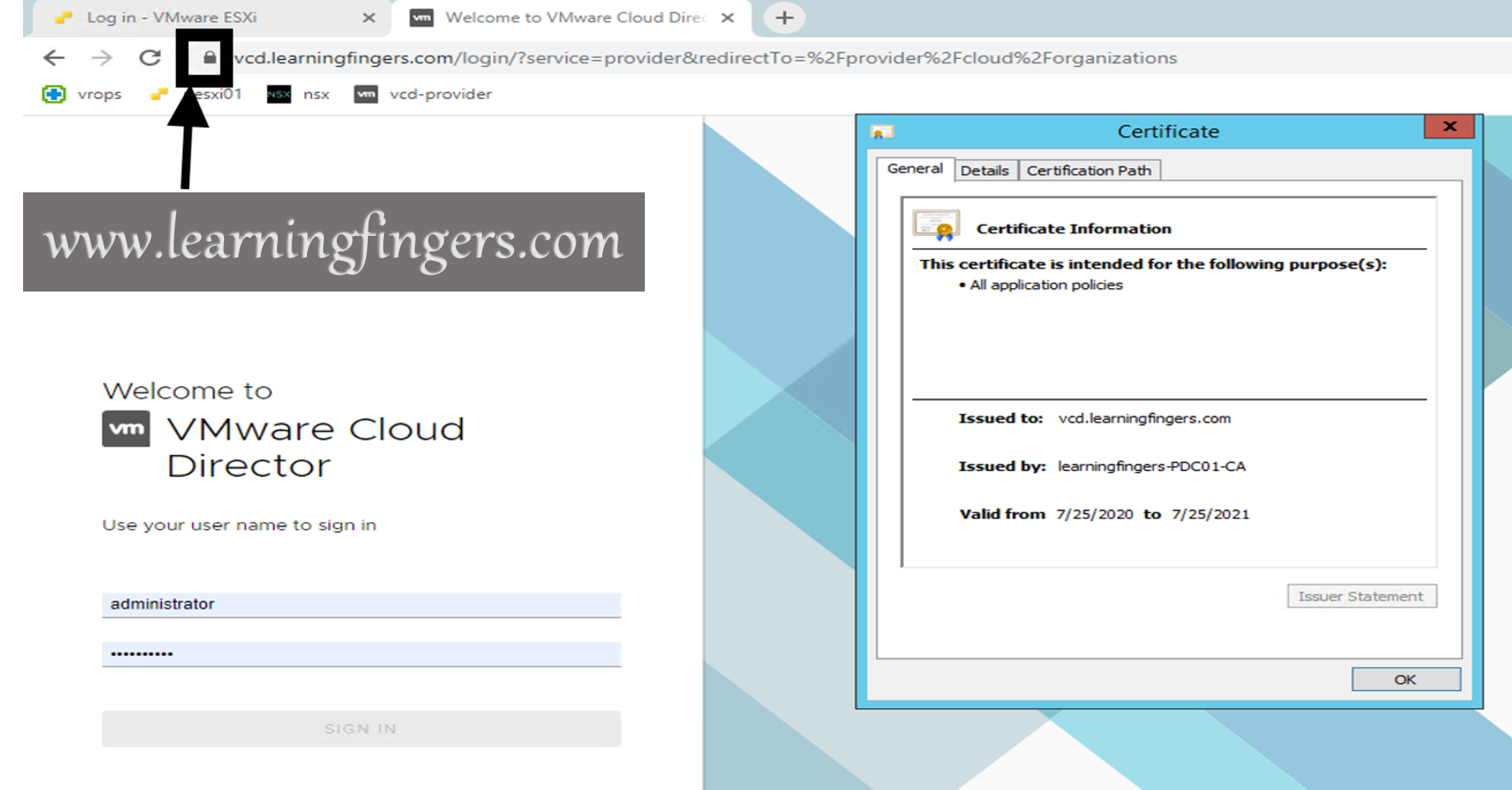
- How to Implement Hytrust KMS and enable vSAN encryption? - 16/10/2022
- How to delete Inaccessible objects in vSAN datastore? - 16/09/2022
- Availability options with vROPs 8. - 04/07/2022