Agenda of this post is to run through the implementation of a KMS solution – Hytrust KeyControl and use it to enable data at rest encryption for vSAN datastore and VM level encryption as well.
To get more clarity on which level of encryption you would need, read VMware official comparison!
Before jumping into the implementation steps, lets quickly review the per-requests and some design consideration:
- VMware doesn’t provide KMS, so you need to choose a KMS solution. Please check the official Compatibility list.
- Data encryption at rest happens for cache tier but while moving to capacity tier, the data is decrypted.
- Deduplication & compression is applied in capacity tier first and then the data is encrypted again.
- I am using Hytrust KeyControl for this demonstration, which is quite easy to implement and use.
- Ensure that the KMS is not deployed in the same datastore which you intend to encrypt.
- Encryption is CPU intensive.
- Keys generated by KMS, is not storage at vCenter – only a list of key IDs is stored.
- if a host rebooted, it does not mount its disk groups until it receives the Key encryption Key (KEK). This process can take several minutes or longer to complete. You can monitor the status of the disk groups in the vSAN health service, under Physical disks > Software state health.
- Download the Hytrust KeyControl with 60 days trail period using link.
- Create DNS record for KMS VM and my lab is vSAN 6.7 U3 based(little outdated)
Step 1: After downloading KeyControl ova, create and power on VM.
Hytrust KeyControl version used here is 5.2.1.
Step 2: Login by browsing URL using DNS or IP address, the default username is secroot and password is secroot. At first login, you will be requested to change the default user’s password.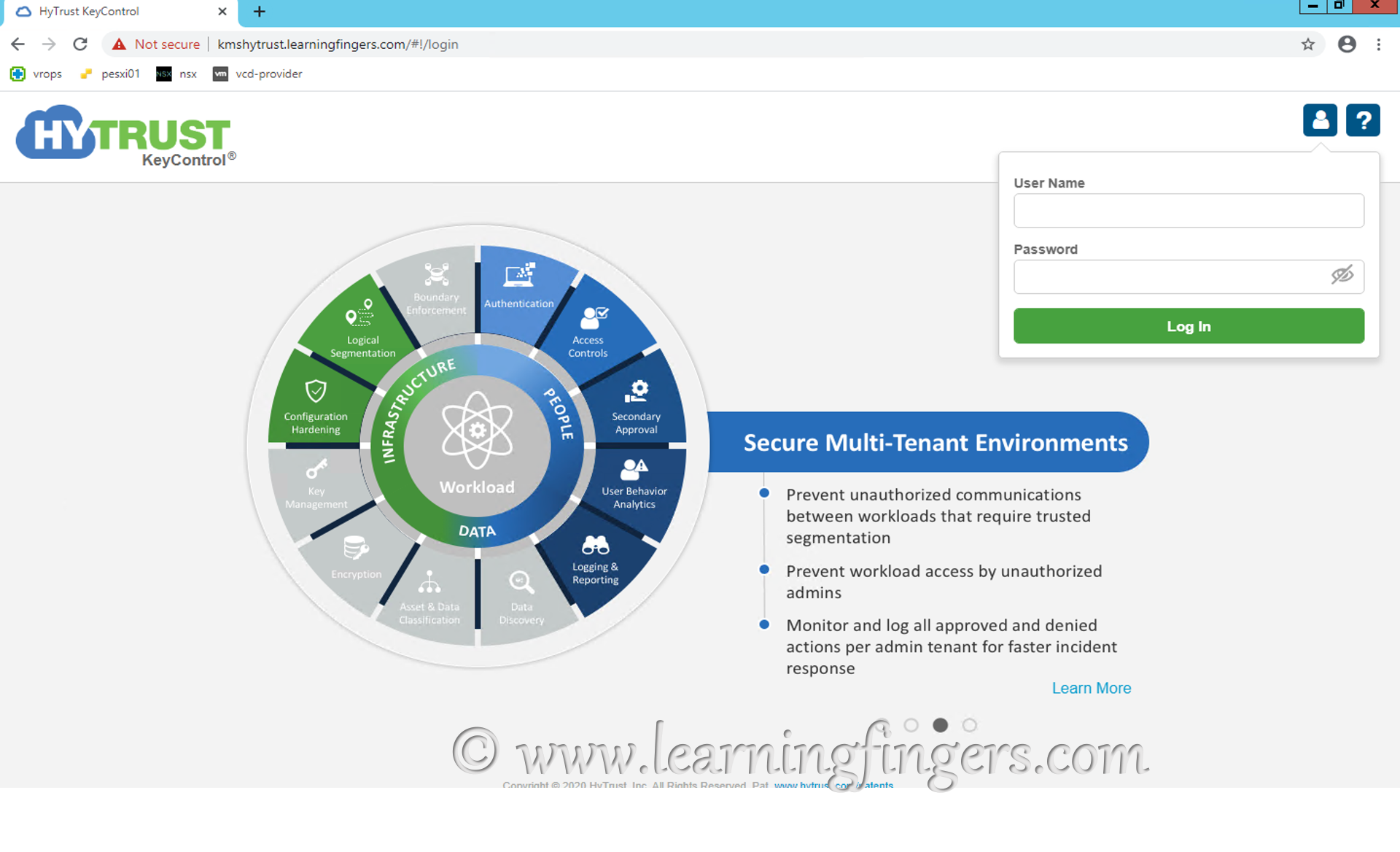
Step 3: Hytrust KeyControl support cluster deployment, this demo comprises of new and single node deployment only. Hence, select Standalone node deployment.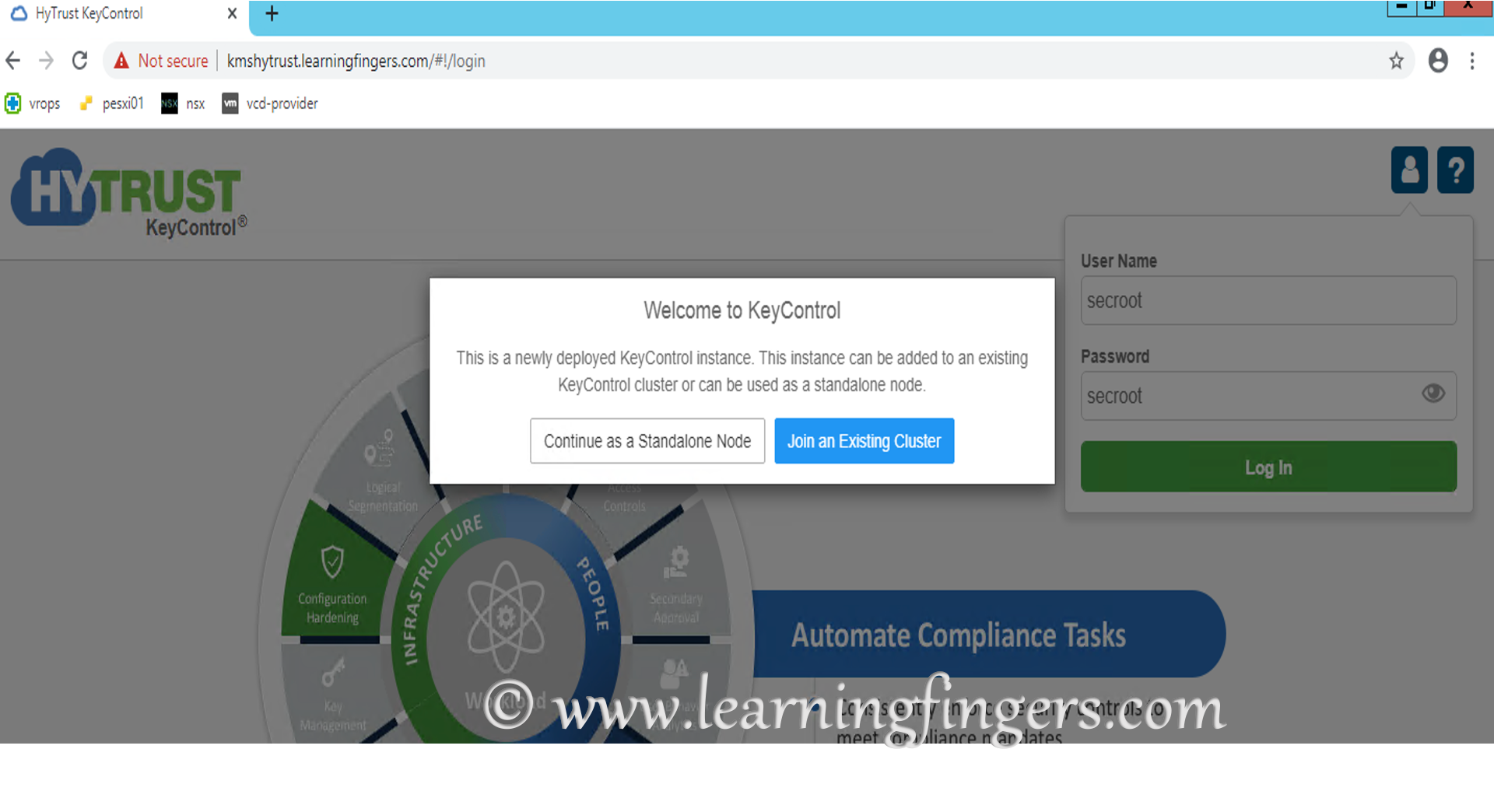 Step 4: As of now, i am skipping the email and mail server configuration.
Step 4: As of now, i am skipping the email and mail server configuration.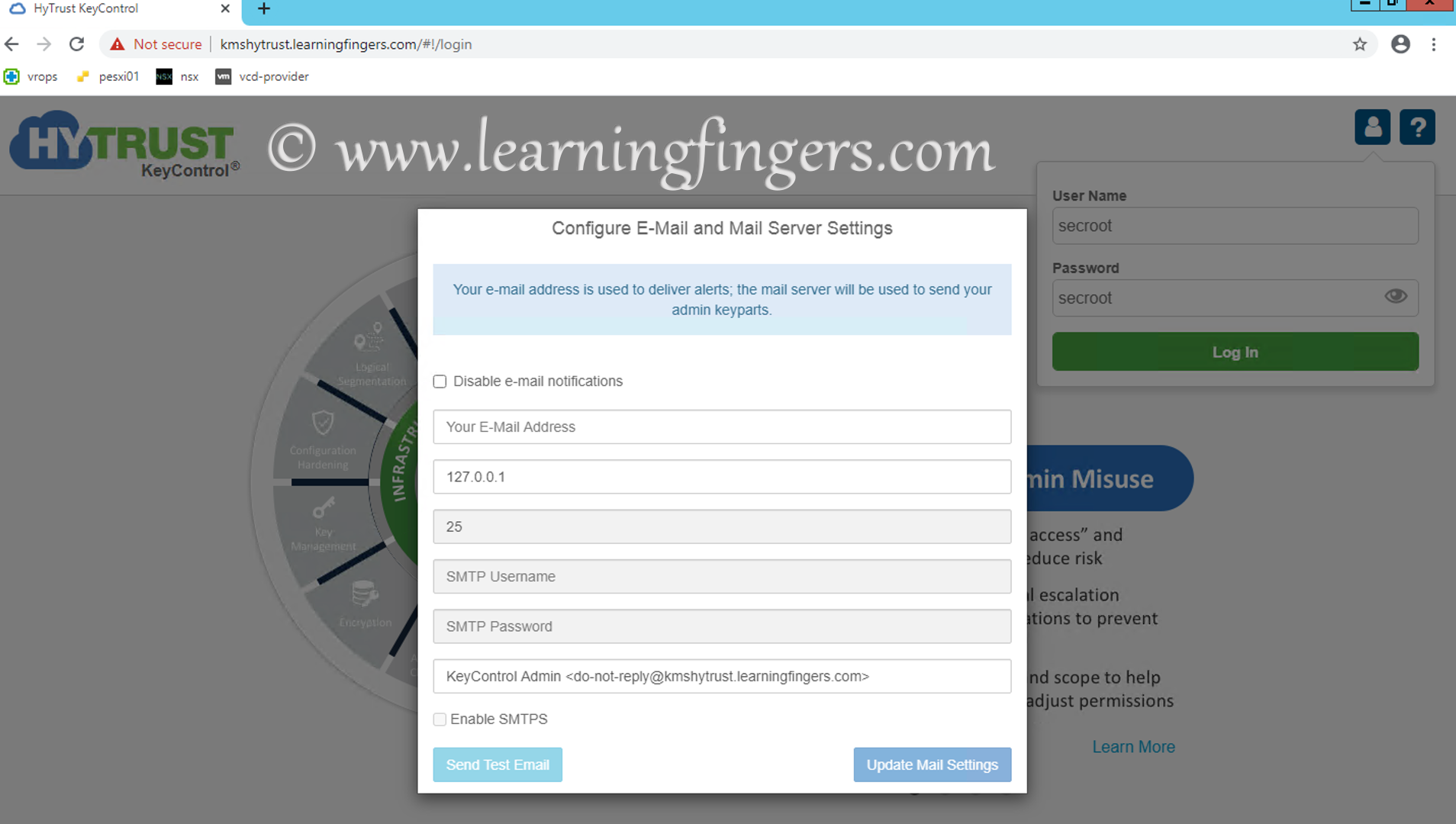
Step 5: Download and save the admin key for future recovery requirement, if KeyControl fails.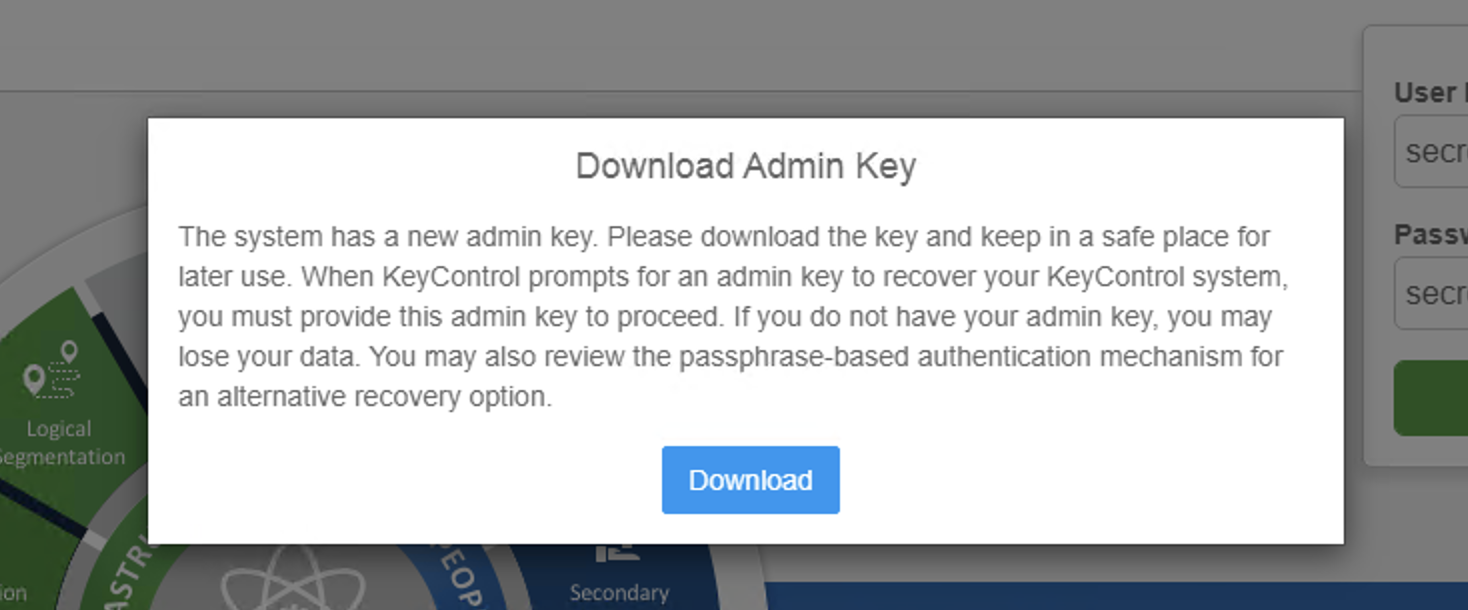
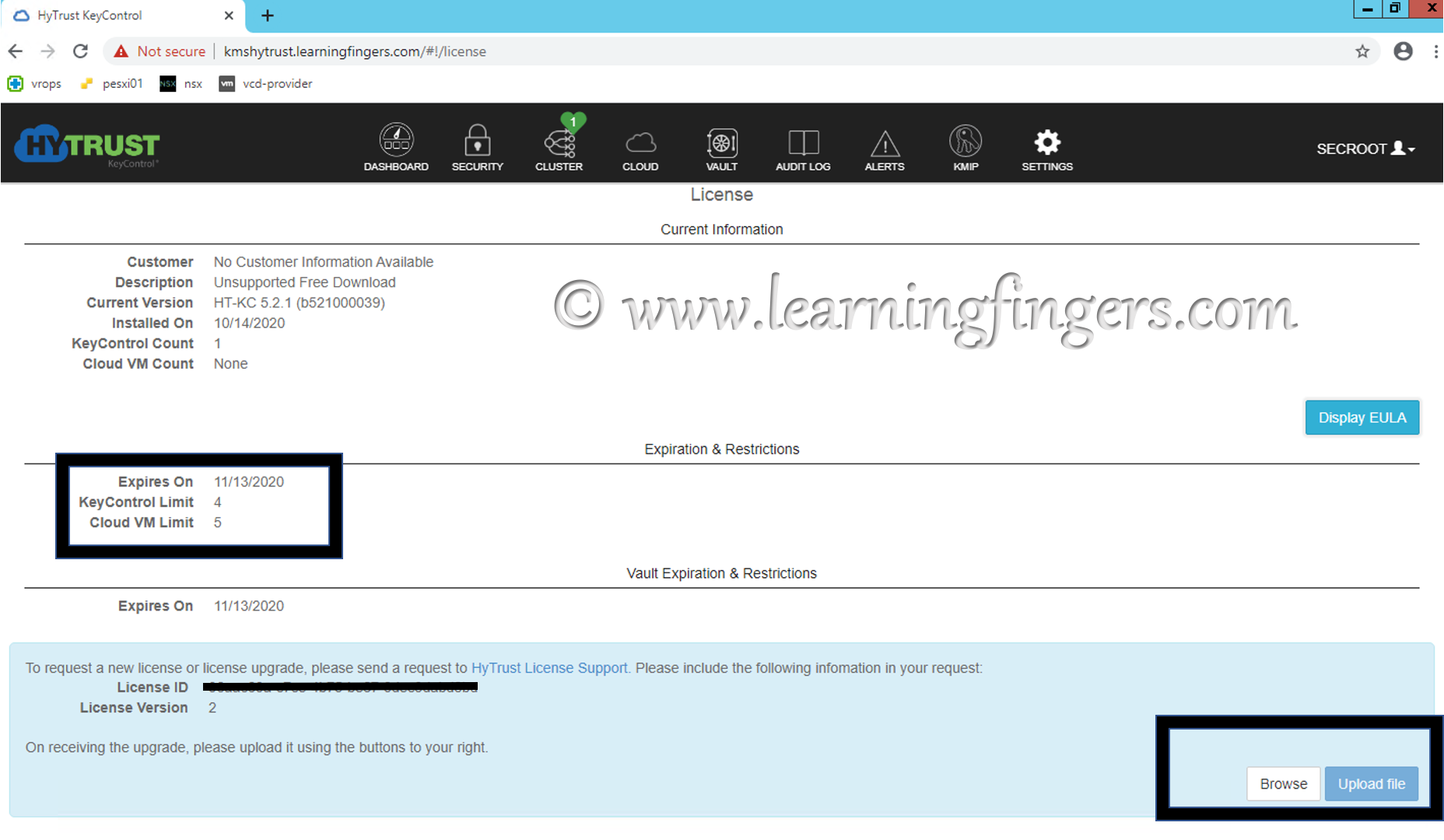
Step 6: Next step should be add the appropriate license or can try the limited quantity on trail version.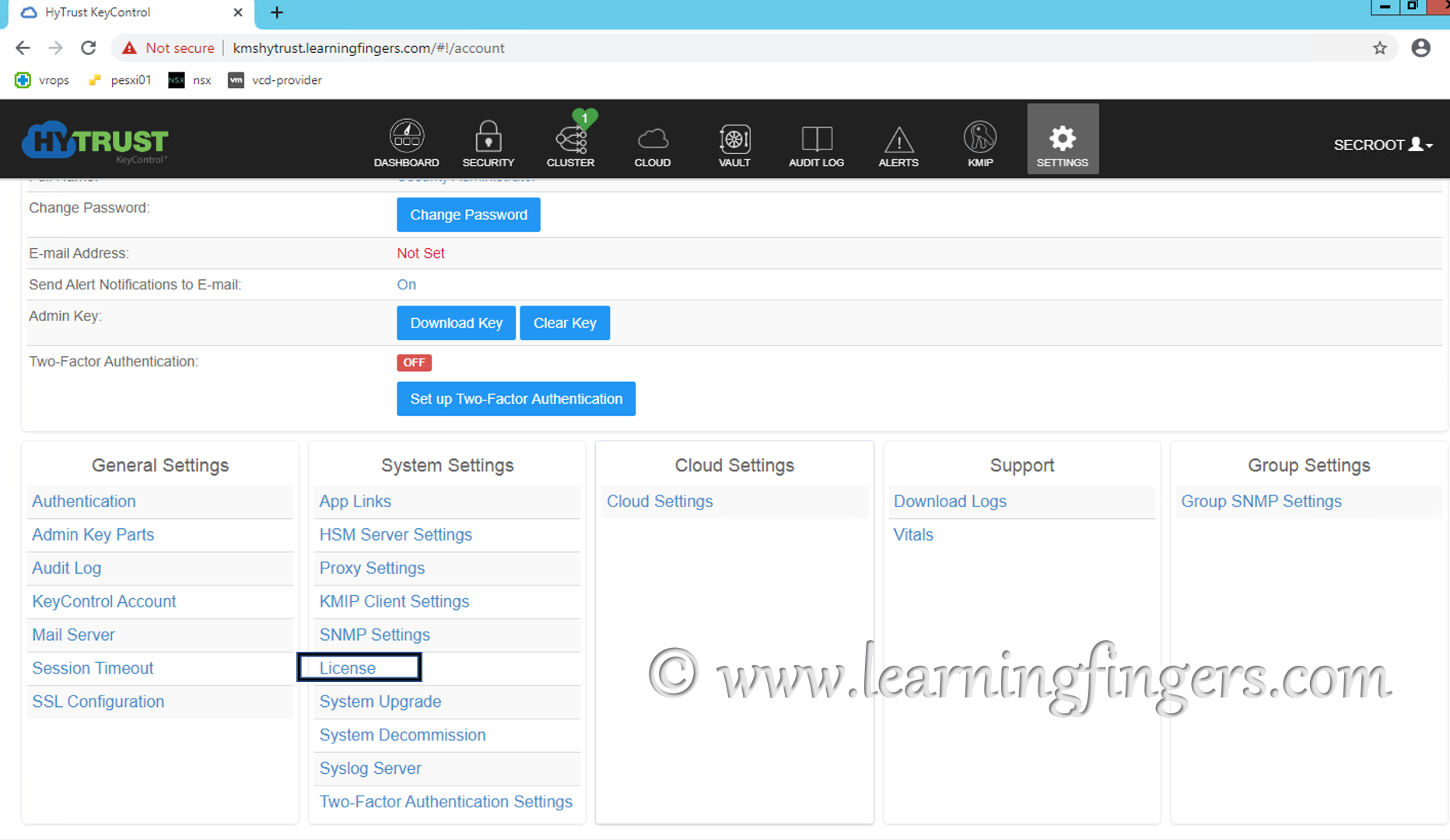
Step 7: Click KMIP -> change the state to Enable -> change the protocol to version 1.1 and apply.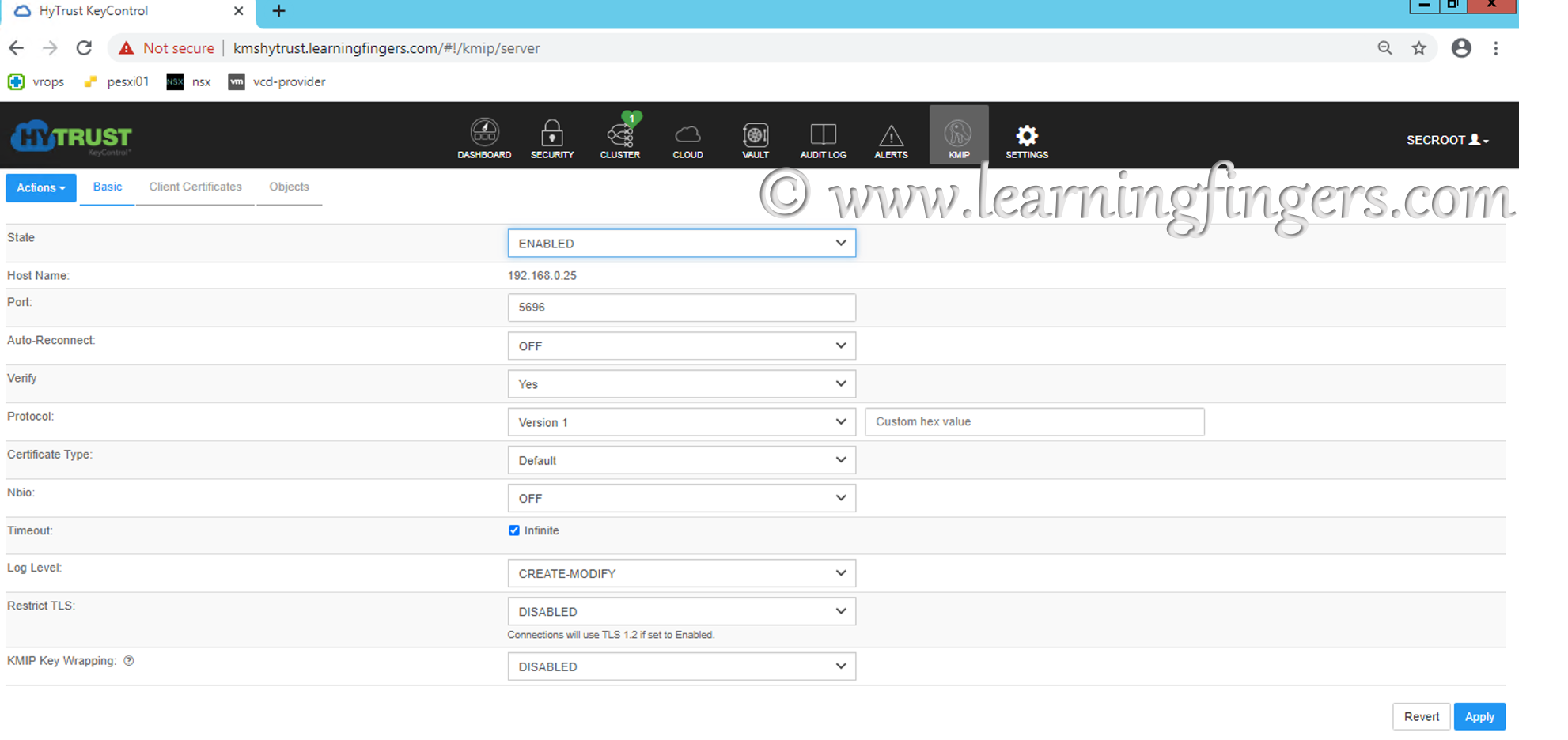
Step 8: Create certificate for integration with vCenter and download it as it will be used in future steps.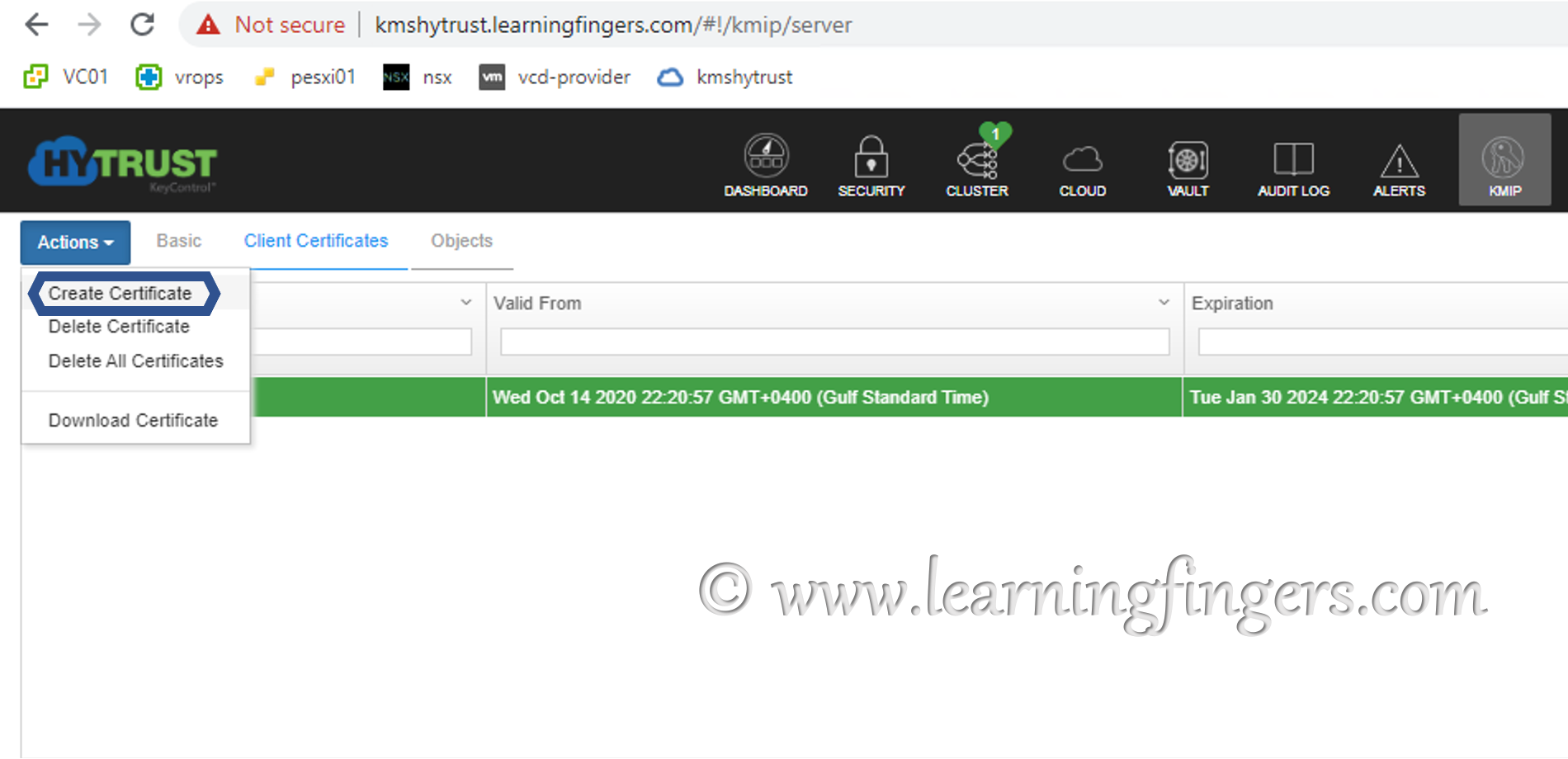
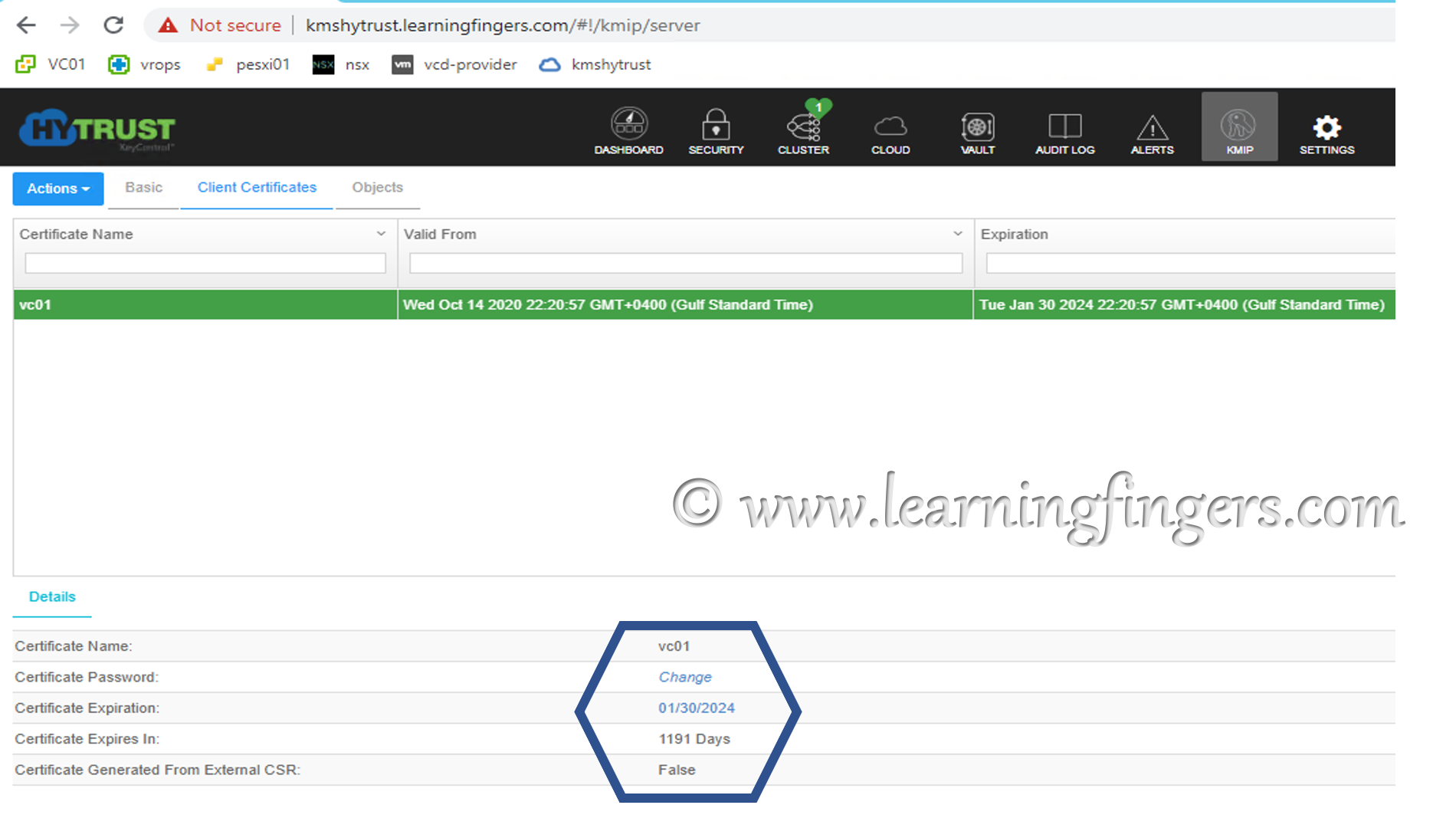
This completes the required configuration from KeyControl side.
Step 9: Login to vCenter and navigate to vCenter – KMS configuration point: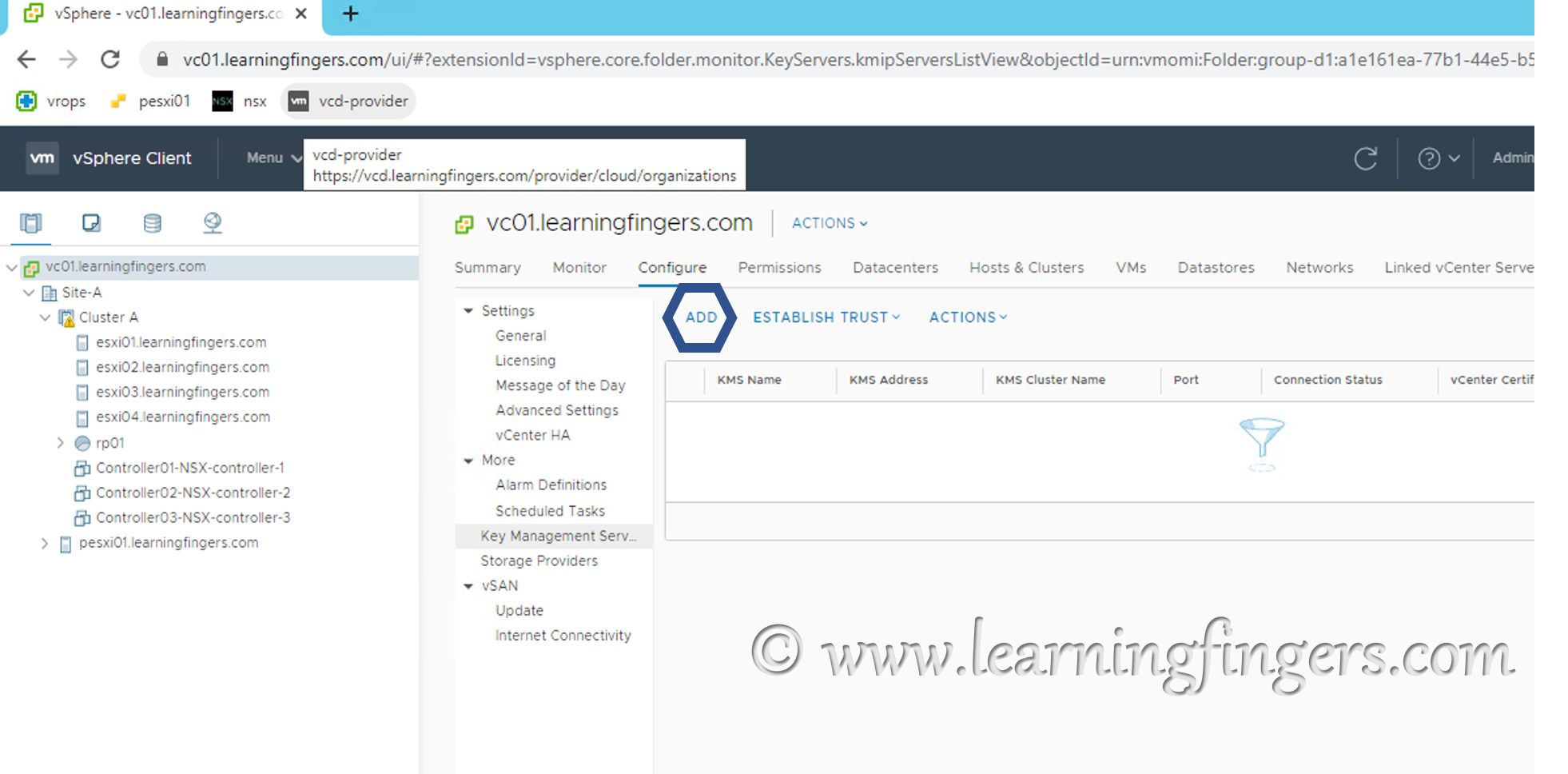
Step 10: Configure vCSA to integrate with KeyControl: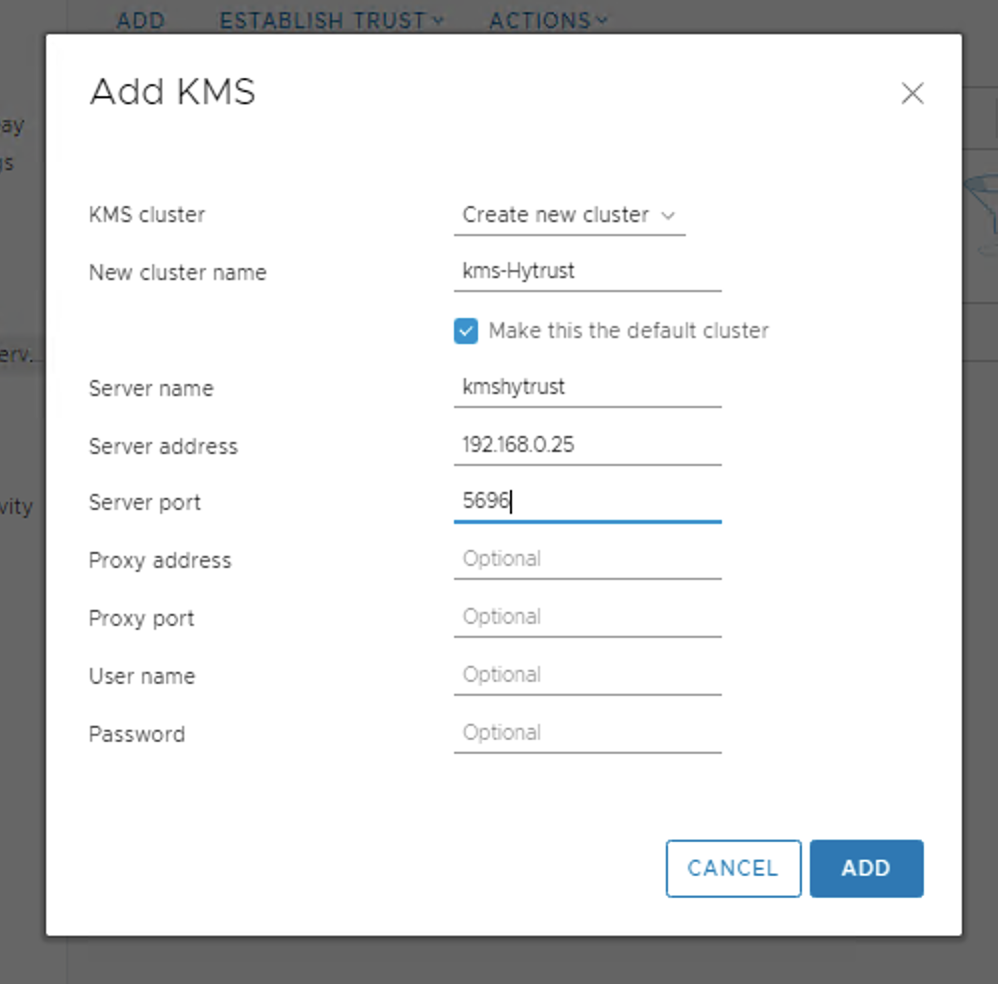
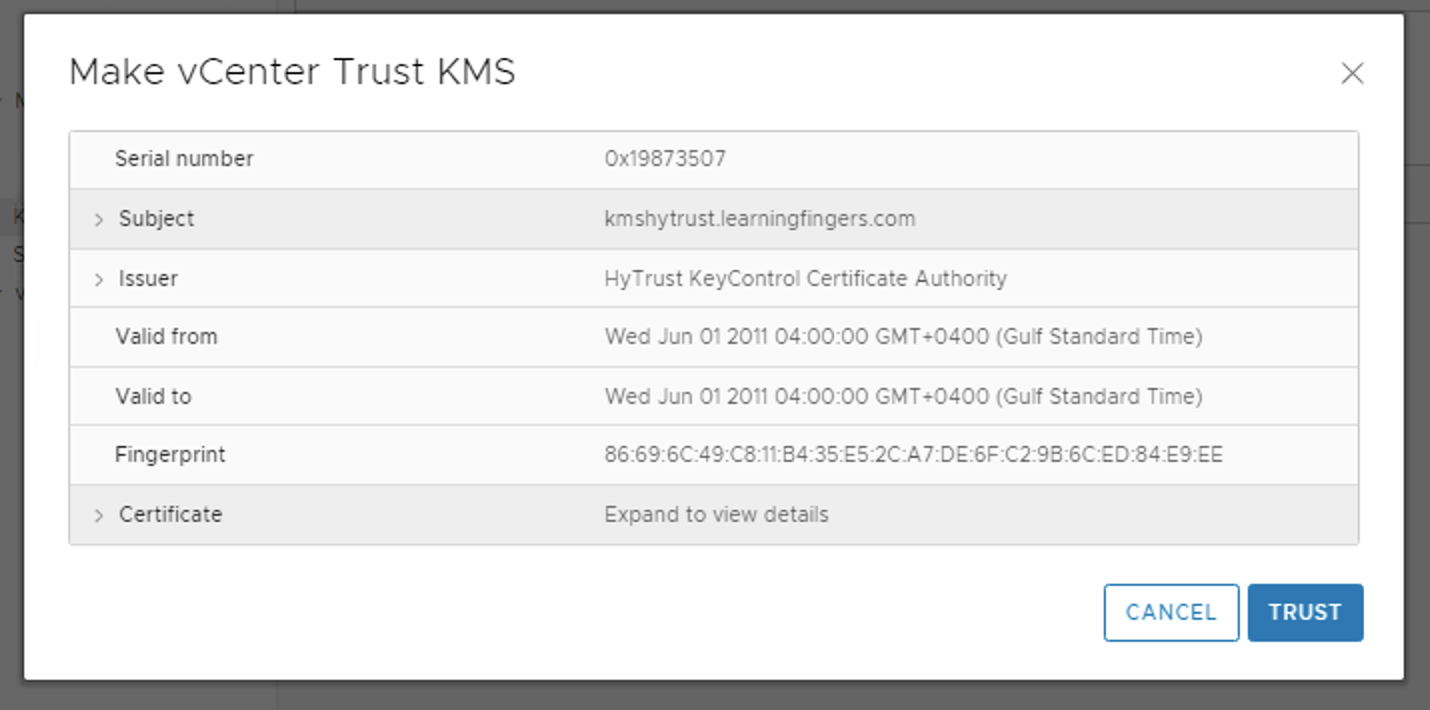
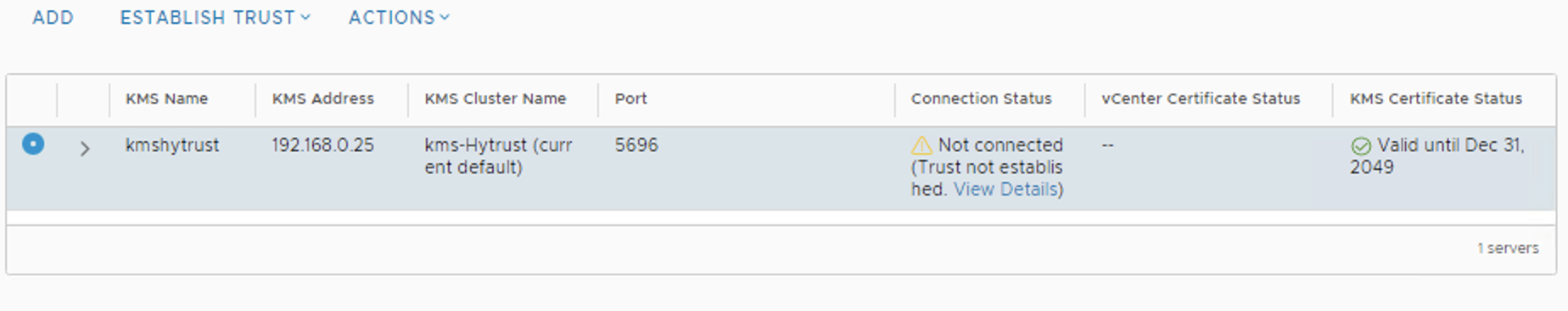
Step 11: From last screenshot you can observe that the KeyControl configuration is done but still connection status is “Not connected”. Reason is certificate, we have to make KMS trust vcenter by providing certificate which we downloaded in step 8.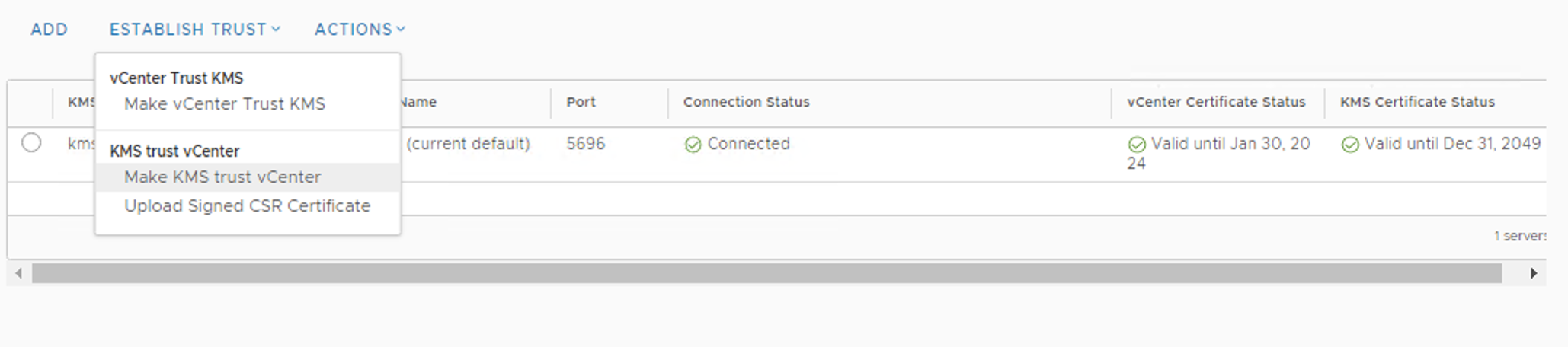
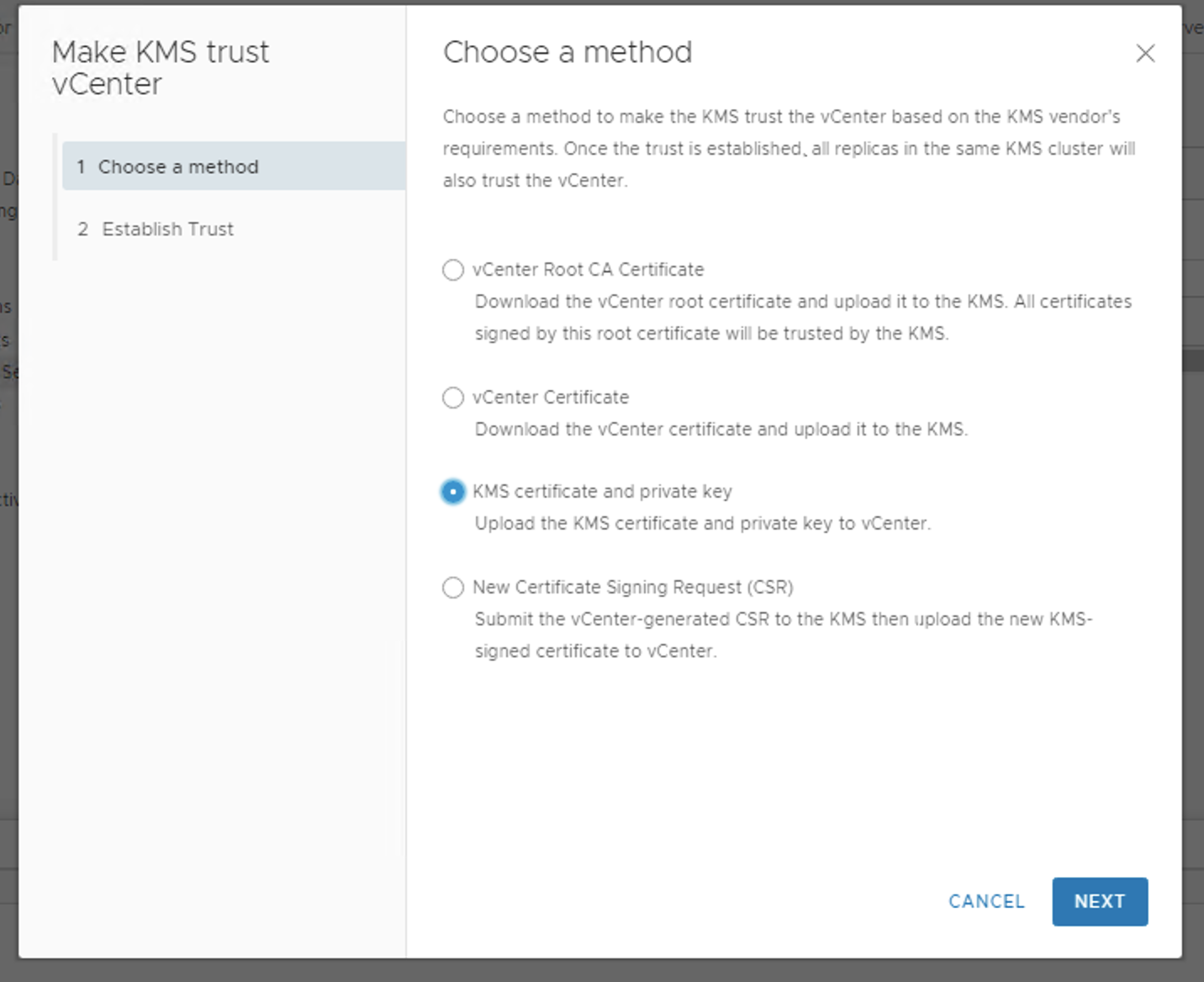
Click upload file and upload the KMS Certificate and KMS private key from the downloaded pem file.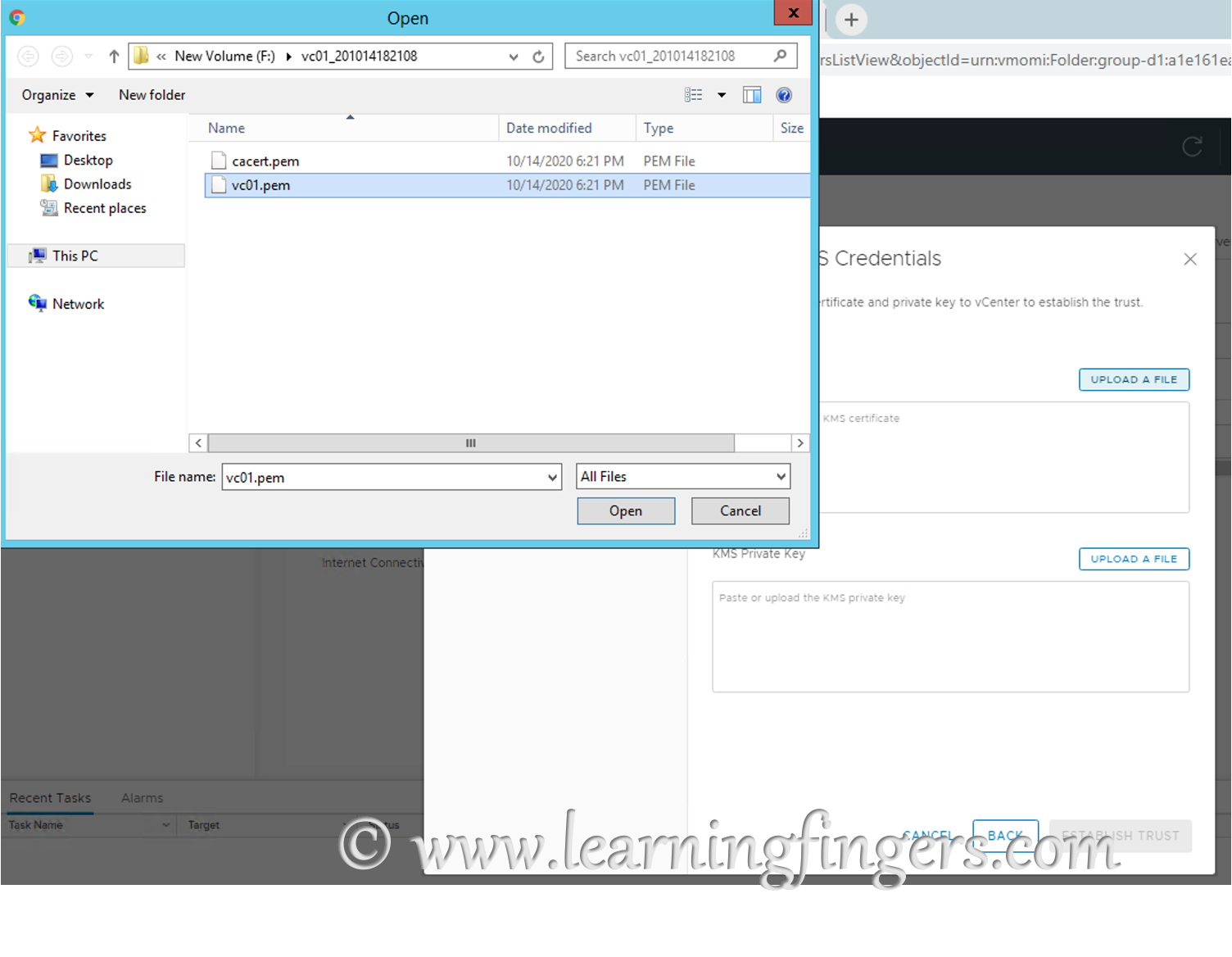
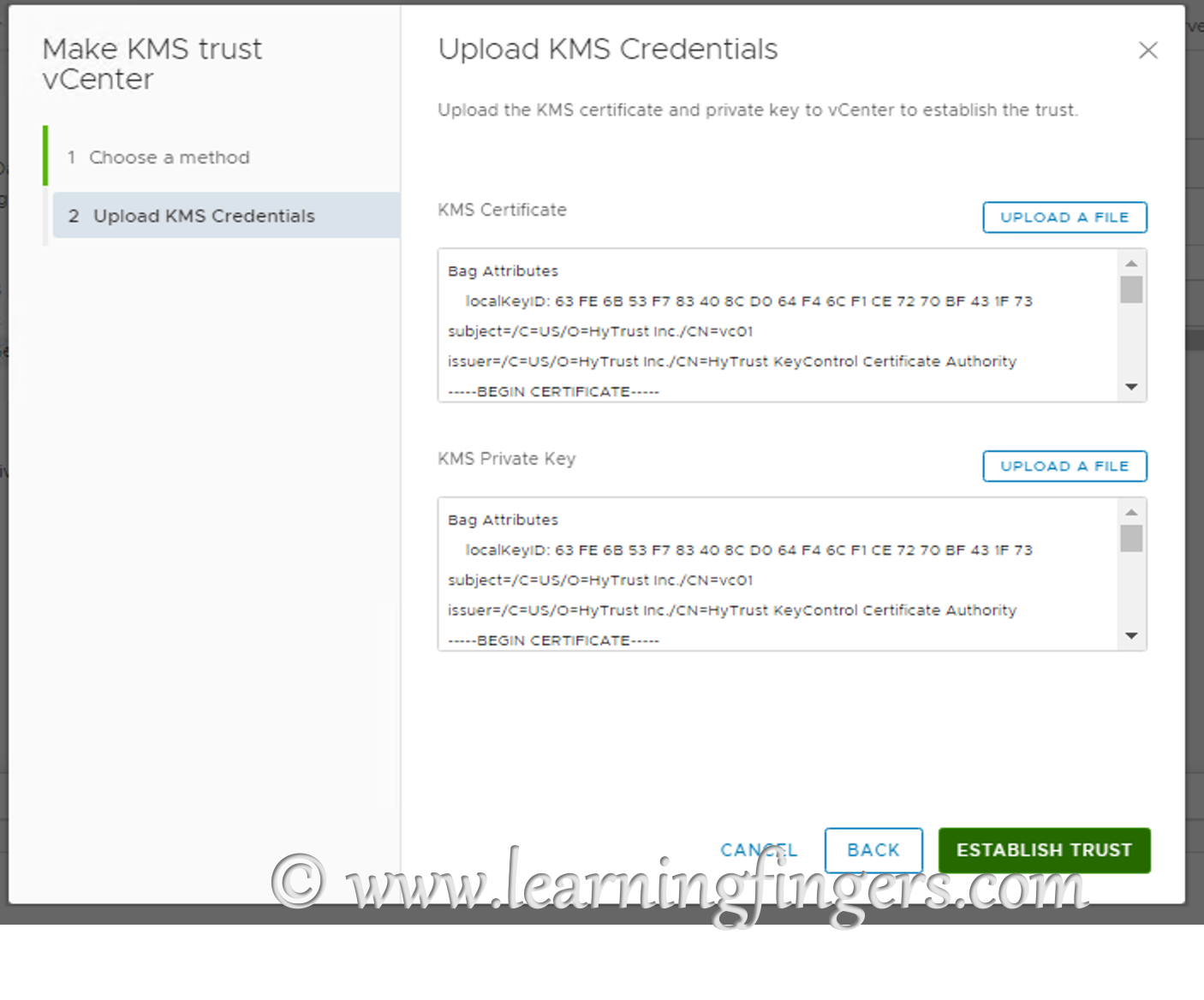
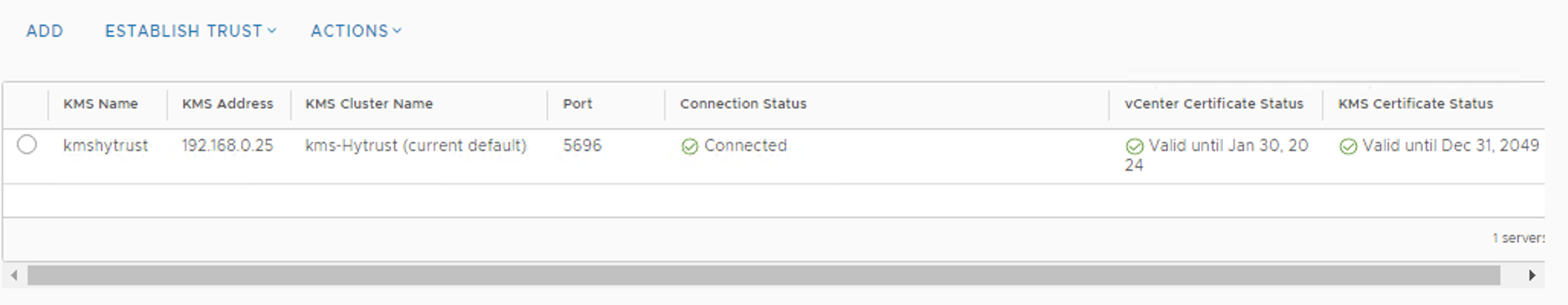
This completes the implementation of Hytrust KeyControl and integration with vCenter.
In upcoming blog post, we will see how we can enable vSAN encryption and VM encryption.
- How to Implement Hytrust KMS and enable vSAN encryption? - 16/10/2022
- How to delete Inaccessible objects in vSAN datastore? - 16/09/2022
- Availability options with vROPs 8. - 04/07/2022